What Is Data Security?
Data security refers to measures taken to prevent unauthorized access to the information stored in computers and databases or on the web, and to prevent the modification or corruption of that information. Data security is sometimes called computer security, systems security or information security, and is an important part of the information technology systems for all organizations, large and small.
What Is Data Security Protecting Against?
The threats that data security protects again are constantly changing and evolving. But there remain some consistent threats, which include the following:
- Security Hackers: People who work to exploit vulnerabilities in a computer system, sometimes for information gathering, protest or theft.
- Malware: A shortened name for “malicious software,” this is software built to gain unauthorized access or cause damage to a computer or computer system.
- Computer Viruses: One form of malware, computer viruses are maliciously written codes that alter how a computer operates and can damage the computer and data stored on it. The code is written so the virus can spread from one computer and computer system to another.
The Need for Data Security: Increasing Hacks, Breaches & Problems
Strong data security has become vital for all organizations as the number of data breaches and other security problems have mushroomed in recent years.
Identity Theft Resource Center, a nonprofit that has been tracking data breaches for more than a dozen years, reported 1,579 data breaches in 2017 — an increase of 45 percent from the previous year. The two areas of the economy that saw the largest increases were general businesses and financial institutions. More than 55 percent of data breaches in 2017 affected businesses, up from 45 percent in 2016.
A separate 2018 study by Thales eSecurity, a data security firm, found that 46 percent of U.S. organizations had experienced a data breach in the previous year, up from 24 percent in the same study the year before. Another study from the PwC consulting firm in 2015 found that the number of cyber security attacks had increased by 38 percent from the previous year, and intellectual property theft had increased by 56 percent.
The cost of data breaches to organizations continues to be staggering. Across the world, data breaches cost companies about $3.6 million per incident in 2017, according to the most recent annual survey by the Ponemon Institute. In the U.S, the average cost for a data breach was $7.35 million per incident, a record high.
Worldwide, data breaches cost $141 per compromised record, according to the Ponemon survey. In certain industries, the cost was much higher — $380 per record in the healthcare industry and $245 per record in the financial services industry.
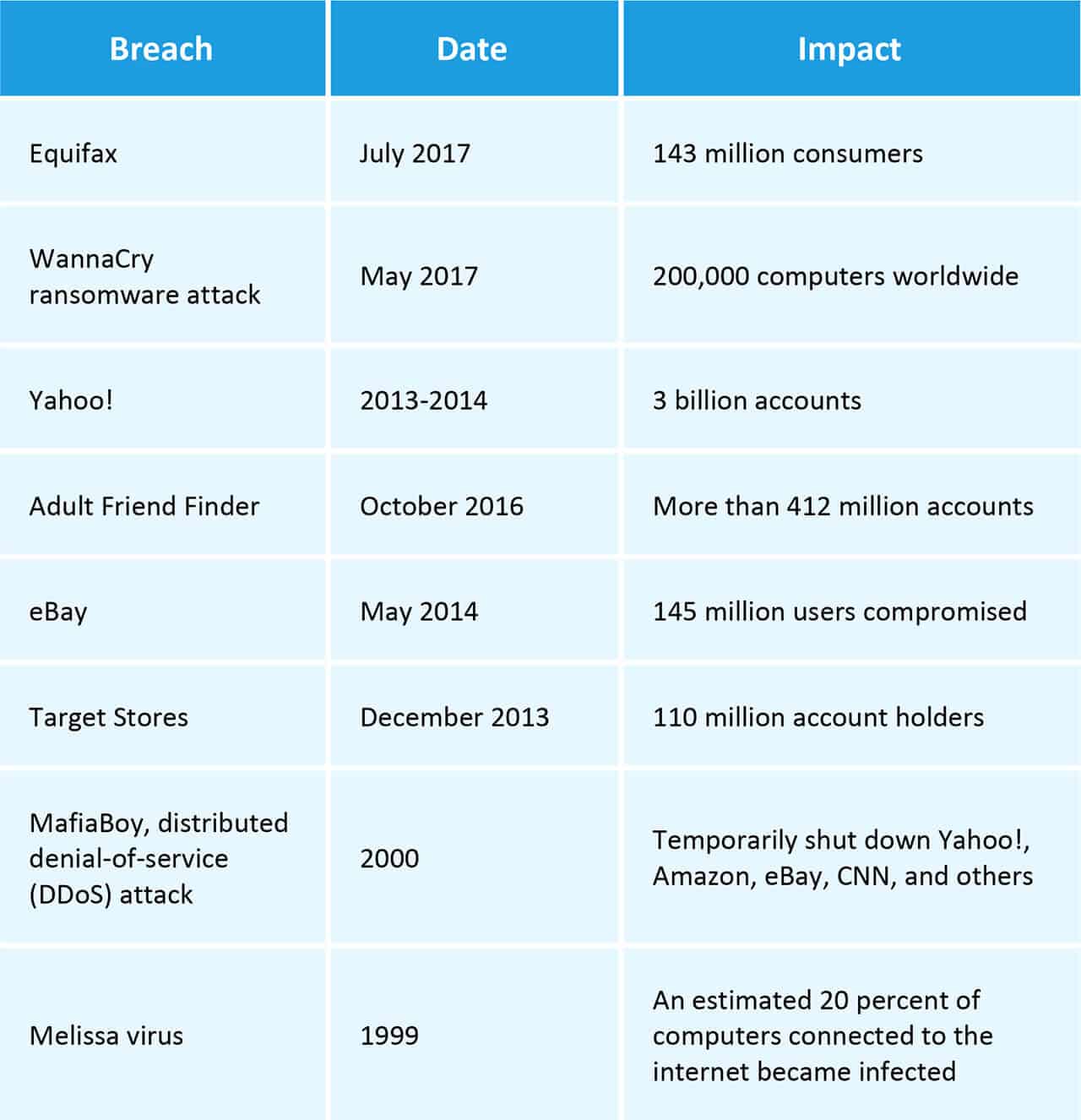
Some of the Largest Data Breaches or Cyber Attacks of Our Time
There have been thousands of known data attacks and breaches over the past several years. Some have been especially large and newsworthy, including the following notable breaches:
Methods Cyber Criminals Use to Infiltrate Computers and Systems
Cyber criminals use a range of methods to infiltrate computers systems. Some have been used for years; others have been developed more recently.
“Every year, the crooks get better and better funded and more and more sophisticated and more and more well organized,” says Russ Schrader, Executive Director of the National Cyber Security Alliance, a nonprofit public-private partnership that promotes cybersecurity and privacy education and awareness.
Among the most common ways cyber criminals infiltrate systems:
- Brute Password Cracking: Hackers can crack some passwords simply by using common or easy-to-guess passwords — like "1234" or "password." They also use computers to quickly try a succession of passwords or move through hundreds of thousands of words. This method can be especially effective if your password is short. A computer can crack a seven-character password in milliseconds. A 12-character password would take about 200 years. If you’re concerned, this site can help you figure out how strong your password is against attacks. Note: Although the site states that it doesn’t collect or store passwords, it’s best not to use your current passwords when trying out the educational tool.
- Using Existing Breached Data: Hackers also use data obtained through unauthorized means, available for purchase online. That existing breached data can give them emails, usernames, and passwords that they can use to gain access to accounts.
- Phishing Emails: You are sent an email, represented to be from your bank, the IRS, or another organization that you do business with or trust. The email suggests the organization needs important information from you and asks you to click on a link within the email. That link takes you to a malicious website, which asks you to enter a user name, password, and possibly other personal information. The hacker then gains access to your actual bank account, or other account.
David Herman is President of RH Strategic Communications, an organization that works with enterprise, public sector, health and cybersecurity companies. He says cyber criminals now are sophisticated enough to learn from online sources who your boss is, and then send you an email seemingly from that boss. Herman explains, “The email says, ‘Hey, I need this right away.’ Then they engage in a dialogue that seems totally legitimate.” With that seeming assurance that the emails are legitimate, you are convinced to click on a link in an email or take other actions that compromise security, according to Herman.
- Vishing (Voice Phishing): A hacker, with access to phone number databases, calls you and represents that he or she is calling from your bank, the IRS or a similar organization. The hacker asks for personal information that they can use to access private data.
“They tell a believable story and someone is convinced that they’re legitimate,” says the National Cyber Security Alliance’s Schrader.
- Smishing (SMS Phishing): You might be sent a text with an embedded link. Similar to phishing, the link is a malicious website designed to extract personal information from you that hackers can use to access your private accounts.
Why Data Security Is So Difficult to Achieve
Data security is so difficult — and personal data is constantly compromised — because of some highly common problems. Some of them relate to the desire to ensure computer systems are easy to navigate for users. Many relate to human nature, or simply to human neglect and ignorance. Here are some of the most common challenges:
- Organizations often have limited knowledge of their own customer data — how sensitive it might be, its location within the organization's computer network, and the risk of unauthorized access to it.
- Organizations don't understand who routinely accesses that customer data. (A 2016 Ponemon study found that only 25 percent of respondents said their company monitors all employee file and email activity.)
- Organizations don't understand how their data is protected, or how to better protect it.
- Organizations don't know when there might be suspicious access to or use of their data, because they don't monitor it closely enough.
- Updates for software that employees routinely use — which often include patches for known vulnerabilities — are not implemented often or soon enough.
- Remote users who access an organization's network remotely are often much more vulnerable to a data breach.
- As an increasing amount of data is stored in the cloud, there can be vulnerabilities in the processes intended to encrypt that data and keep it secure.
- Internal risks from authorized users who can inadvertently or intentionally cause significant data breaches.
- Organizations want to maintain ease of use of their systems for authorized users — while trying to provide good security.
- As the range of data collected grows, along with its use, organizations must implement new and broader security measures to accompany that growth.
- Data is often spread across an organization, with computer system hardware often in a range of places.
- Unstructured data — data that is not in fixed, easily searchable fields within a database — now makes up 80 percent of all data and can be more difficult to monitor and protect.
Special Data Security Challenges Relating to Mobile Devices
Almost everyone now carries a cell phone, and many others routinely use tablets and personal laptop computers. These ever-present mobile devices pose particular problems for your organization’s data security. The following are among the most common challenges:
- Mobile devices, owned by an organization's employees, will often have access to your organization's computer network — even though they don't normally have the data security protections that are vital to your network.
Herman, from RH Strategic Communications, explains that while your organization may have sophisticated passwords and authentication requirements for its network, it is all compromised when an employee’s mobile phone has easy access to the network — which is then all reachable by someone guessing the phone’s 1-2-3-4 password.
- Mobile devices are frequently shared with others temporarily. That means those others may not follow your organization’s procedures for use of mobile devices relating to their data.
- Applications for mobile devices are often connected to web services, which makes it easier for the unauthorized transfer of data.
Increasing Concerns About Data Security Mean the Market for Experts Is Growing
The data security challenges that all organizations face mean the market for experts to help them continues to grow. A 2017 Gartner report estimated that worldwide spending on data security products and services would reach $86.4 billion in 2017, and an estimated $93 billion in 2018.
What Is Data Security Management?
Data security management is the effective oversight and management of an organization's data to ensure the data is not accessed or corrupted by unauthorized users. A data security management plan includes planning, implementation of the plan, and verification and updating of the plan’s components.
Additionally, the following are basics of data security that are often included in any data security management plan:
- Backups: Continual backups of data ensure the ability to recover lost data.
- Data Masking: A process in which some data is obscured so sensitive information is not exposed. Data masking might be necessary when technicians need to work with the data to develop applications or conduct text cycles.
- Data Erasure: A method in which data on a hard disk or other digital media is overwritten or wiped clean when the equipment is sold or discarded.
- Encryption: The process by which data is scrambled and encoded to make it unintelligible. Only another entity with the encryption key can decode the data. Encryption is an important method for ensuring data security, especially for data that moves across computer networks.
- Authentication: The process of determining whether a computer system user is who he or she claims to be. Usernames and passwords are a common authentication method.
- One-time Password: A password that works for only one network session or transaction. One-time passwords enhance digital security because intruders who could gain access through the discovery and reuse of a traditional password can't gain that access.
- Electronic Security Tokens: Physical devices that serve as an electronic "key" to allow a user to gain access to data or to a physical place. Digital information is stored on the devices. The user may need the device along with a separate password to access the resource.
- Two-factor Authentication: A requirement of two methods to authenticate an authorized user. For example, two-factor authentication might require a password from the user, along with information only they would know, or a password along with an electronic security token.
- Transparent Data Encryption (TDE): A method that encrypts the actual files of a database, rather than the data. An authorized user has normal access to the data, and may not be aware of the use of TDE. The method ensures that an intruder who gets access to all of the data can't read it or use it when it's placed on a different server.
- Cloud Access Security Broker: Software that works between users of a cloud service and the cloud applications. The software monitors activity and ensures the user's security policies are followed.
- Active Directory Rights Management Services: Use of this Microsoft Windows security tool (formerly called Windows Rights Management Services, before Windows Server 2008) helps organizations set and manage the kind of access users have to an email message, Microsoft office documents, and other information on the Windows server.
- Big Data Security: Big data refers to the extremely large amounts of data (in all forms) that can be gathered, analyzed, and mined for information. Hadoop is an open source software platform that you can use to store and process extremely large sets of data.
- Internet of Things (IoT) Data Security: Safeguards that are part of, or added to, devices that are part of the Internet of Things. The IoT are the billions of everyday devices that are embedded within computing devices, from refrigerators to oil-drilling equipment. Those computers enable them to send and receive data that help them operate.
- Payments Security, Mobile App Security, Web Browser Security, Email Security: Each of these modes of computing and data transfer have special security features that work to prevent unauthorized access.
Data Security Best Practices
When it comes to managing your organization data and enhancing its security efforts, there are many steps that you can take to get started. Some of the suggested steps to take include the following:
- Understand the data you have, what data is the most sensitive, and how it is being secured. Many organizations don't fully understand the data they have, how sensitive some of it is, and how it is stored and protected. Therefore, companies should undergo a formal process that provides that understanding, and then perform a risk analysis to determine what data might especially be at risk and how to protect it. Then, establish a data security plan that outlines how your organization will assess and protect its data.
“Never forget what you are really protecting,” says Raef Meeuwisse, author of Cybersecurity for Beginners and the forthcoming book How to Hack a Human. “There is a reason that the discipline is called information security. Yet, in almost 99 percent of audits, I find the organization has no definitive asset list of their information of value. If they don’t know what their information of value is, or where it flows, then of course, they cannot make it secure.”
Data Security Plan Template
Get started building a data security plan for your organization. The customizable template provides guidance on vital actions your organization should take to help keep its data secure.
Download Data Security Plan Template - Word
- Collect and keep only the sensitive/private information you need about customers or contacts. Organizations often collect more information from customers and contacts than they actually need, and keep it longer than they need it. Only collect the information you need to help your business, and institute a process that deletes the information when it is no longer needed.
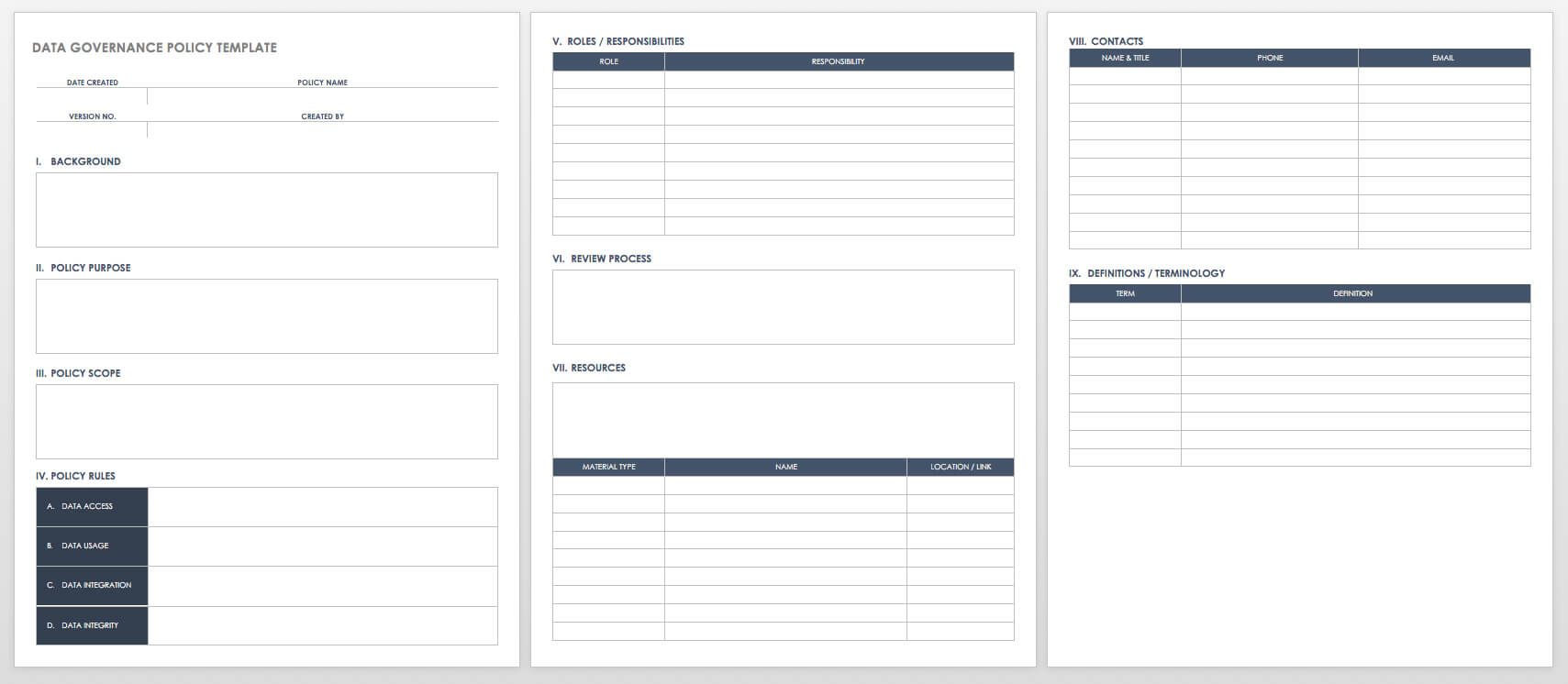
- Establish effective data governance. Data governance is the overall structure that an organization sets up to properly manage its data. That structure establishes the authority and the shared decision-making that are vital to how the organization properly uses and manages its data.
Data Governance Policy Template
When establishing data quality and reliability standards, you should create a data governance policy that everyone in the organization can follow. You can use this template to build that policy and create standards associated with accessing, storing, and backing up data.
Download Data Governance Policy Template - Word
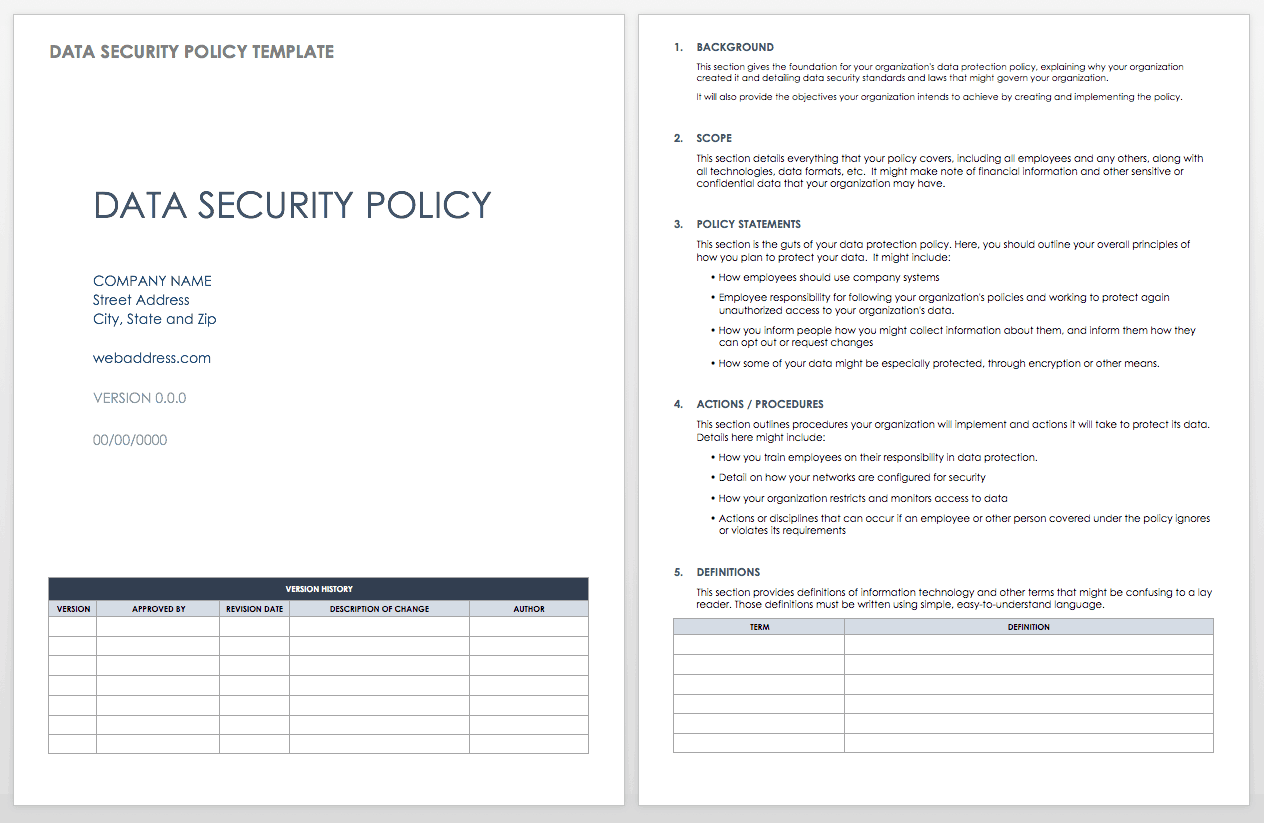
Data Security Policy Template
It’s important that your organization explain in writing the policies it has established to keep its data safe, including how it informs people that it is collecting data about them and requests their consent, how sensitive data is provided extra protection, and how employees are expected to appropriately work with data and keep it safe. This template can help you start outlining some of those security policies.
Download Data Security Policy Template - Word
- Establish password and authentication policies that are rigorous and enhance security. A 2016 Verizon report found that 63 percent of data security intrusions came from passwords that were default passwords, were easily guessable, or were stolen. Requiring effective passwords, and in some cases two-factor authentication, significantly improves your data security.
“For passwords, use something long and easy to remember,” advises the National Cyber Security Alliance’s Schrader, who suggests a several-word phrase that the user will remember. “That makes it hard for a brute force computer to break down."
Herman of RH Strategic also recommends organizations more often use two-factor authentication. That might mean a user needs to quickly identify an image sent, or use a simple code sent to their mobile phone. “Organizations are afraid that it’s going to make it more difficult for employees to access,” Herman explains. “But the truth is it probably adds one second. Maybe over the course of an entire day, it adds a minute.” And, it increases data security tremendously, he says.
- Educate employees: Everyone is a part of data security. Data security is a job for people far beyond your IT department. All employees should read and understand your organization's policies on data security. You should try to ensure that all employees understand, among other things, what data is confidential and what rules they must follow in accessing your network — including from remote locations. They should also understand threats of phishing emails and social media accounts.
- Establish policies on mobile phones and other mobile devices. Mobile devices — especially the mobile phones that all of your employees use every day — can represent a significant threat to your system's data security. If your organization provides your employees with mobile phones or other mobile devices, you should set policies on how they can be used and when, if ever, those employees can install outside applications to the devices. If you allow employees to use their own devices to access company data or the company email system, you should have a process to ensure those devices have adequate encryption and other security measures in place so they are not a threat to your organization's data.
- Protect all data by default. A significant problem with data security is that once an intruder breaks through the outer "wall" into a computer network, he or she often has easy access to the data within that system. More and more experts are recommending better security throughout the system. For example, transparent data encryption ensures that the actual files and organizational structure of a database are encrypted — not just the data. Organizations are also creating a safe zone, where only applications and computers they trust are allowed access to the data. They "trust" based on digital analysis of the user's apparent identity, location, and other distinguishing data.
- Use an ad blocker on every device your network. Not only will an ad blocker make employees more productive, but it will also ensure that employees don't inadvertently open a pop-up ad that could be fraudulent and lead to a data breach.
- Stay updated on known vulnerabilities. Computer experts throughout the world are always finding new vulnerabilities to computer networks and software. It’s also a good idea to continually stay updated on those known vulnerabilities.
- Stay apprised of the latest data security threats worldwide. Beyond known vulnerabilities, your IT professionals should stay updated on all of the latest data security threats known worldwide. Free online community forums and resources like CVE can help.
- Hire a hacker. Even companies that think they're doing a good job with data security cannot trust that their system is secure — they should continually and intensively test that security. Many organizations actually hire “white hat” hackers to attack their networks to see what weaknesses a hacking expert would be able to find and exploit.
- Immediately fix any vulnerabilities you discover. Keeping track of your possible vulnerabilities and data security issues in general will do no good if you delay in acting on what you find. Experts suggest you ensure your team quickly implements software updates that will have patches to known vulnerabilities and immediately make other needed fixes after checking your own system’s vulnerabilities and as your IT experts keep track of data security in general.
- Have an emergency plan and follow it closely after any data breach. The Ponemon Institute's annual "Cost of Data Breach Study" has routinely found that the most important factor in lowering costs from a data breach are discovering it and fixing it as quickly as possible. That means continual monitoring of your system and having an incident team ready — either an internal team or external group contracted to immediately help. You might consider performing a test drill with a simulated attack to see how well your response plan works.
What Are Data Security Standards?
Data security standards are rules that apply to data security within some countries, governmental organizations, and industries. There are also standards — for instance the ISO/IEC 27001, from the International Organization of Standards — that are voluntary but specify in detail best practices to keep data secure. Organizations that apply the standards can receive special certification.
Some notable standards:
- FIPS 200: FIPS 200 (which stands for federal information processing standards) sets minimum security requirements for the U.S. government's information systems.
- NIST 800-53: Originated from the National Institute of Standards and Technology, NIST 800-53 sets detailed cybersecurity guidelines that supplement FIPS 200. The guidelines are voluntary but are commonly followed by many organizations.
- PCI DSS: Standards for the payment card industry that try to ensure data security of holders of credit and debit cards.
Laws That Govern Data Security
A number of countries, including the US, have enacted various laws that govern data security in certain jurisdictions and within certain industries. Below are some notable examples. Please keep in mind that the information below is provided for informational and educational purposes only and is not intended as legal advice — you should consult with your own attorney to determine if and how these laws apply to you. You should not rely on this as legal advice or as a recommendation of any particular legal understanding.
- The UK Data Protection Act of 1998: The United Kingdom Parliament approved a law requiring certain data security measures to protect personal data stored on computers.
- Gramm-Leach-Bliley Act: This law, passed by the U.S. Congress in 1999, included a number of major provisions dealing with banks and financial institutions. An important provision requires financial institutions, including investment advisers and insurance companies, to safeguard sensitive personal data, explain to customers how they share information and how customers can prohibit their information from being shared.
- Health Insurance Portability and Accountability Act (HIPAA): This U.S. federal law, governing health institutions and those who do business with them, includes a privacy rule that requires certain data security safeguards to protect people's personal health information.
- Health Breach Notification Rule: This U.S. federal law governs businesses that may How do you normally handle the disclaimer language?have individual personal health information but aren't governed by HIPAA. It requires those businesses to notify their customers, the Federal Trade Commission, and in some cases the media if there's a breach of that health information.
- New York State Cybersecurity Regulations: Beginning in 2017, financial institutions regulated by the New York Department of Financial Services are required to have comprehensive security in place to protect their customers' private data.
- General Data Protection Regulation of the European Union (EU): This regulation, which is also known as GDPR, went into effect on May 25, 2018, and requires that organizations that process personally identifiable information of individuals take certain measures to ensure individuals know what information about them is being collected and that they consent to the collection, use, and processing of that information. The GDPR also grants individuals a number of rights in relation to their data including the right to be informed, right of access, right of rectification, right to erasure, right to restrict processing, right to data portability, right to object, and right in relation to automated decision making and profiling. Since the regulation applies to any entity that has personal information on a resident of the 28 countries of the EU, it is in effect a worldwide regulation and will govern most multinational corporations, including companies like Facebook and Google.
Understanding the Difference Between Data Security and Privacy
Data security and privacy are closely intertwined. But the idea of privacy is larger than simple data security, and it's important to understand the difference.
Your organization can comply with all rules and regulations relating to keeping data secure. But it can still then use people's personal data — tracking their location, gathering information on people in their electronic address books, tracking their emails — in a way that some people believe violates their privacy. Your organization should have policies on how personal information is used, how people are told their information is being used, and how they can give, decline or revoke their consent.
Improve Information and Data Security with Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.