What Is Cyber Security All About?
Cyber security is the processes and methods that secure computer devices, networks, and data and information against attack, theft, misdirection, misuse, or disruption. Cyber security’s purview extends to considerations of the nature and source of threats and the infrastructure beyond an internal network. The cyber security field also covers issues surrounding public computer policy including network policy, cyber threat awareness, and threat information sharing.
Cyber security is a superset for many aspects of security, including network security. However, network security focuses on protecting the internal data and infrastructure of a small or enterprise-sized organization, and manages access control, passwords, firewalls, scans, and antivirus software. Cyber security also encompasses the following aspects:
- Application Security: An effort to build robust security features into applications, especially those that are available through the internet.
- Information Security (InfoSec): The processes, policies, and tools that secure digital and nondigital data and information from attack and misuse.
- Operational Security (OPSEC): The goal of OPSEC is to identify and determine methods to protect assets. Operational security usually consists of five steps: identify assets, identify threats, determine vulnerabilities, assess risks, and invoke countermeasures.
- Disaster Recovery and Business Continuity: Disaster recovery anticipates security events and provides a plan for recovering assets and resuming business.
- Enduser Education: Good cyber security practice empowers every member of an organization to recognize and resist security threats.
What Is Computer Security?
Cyber security has a few synonyms, computer security and IT security, which may sound more approachable for non-technical people. The goal of computer security is to protect hardware, software, and the data they store and transmit from potential damage, disruption, or misappropriated use.
Why Is It Important to Have Cyber Security?
Everything is digitized and online, from banking to maintaining friendships. Cyber security concerns have moved beyond protecting traditional desktop computers and server farms and the confidential or personal identifying information (PII) they contain. Security must protect millions of smart devices that perform every activity, from remotely adjusting the temperature in your office to changing traffic signals to ensuring water flows through mains at a steady rate.
The integration of digital and information technology is increasing at home, work, and even in public infrastructure. As government cyber security sites note, hackers (whether amateurs or organized criminals) want to deny, destroy, degrade, and disrupt our networks.
There’s no sign that threats and crime will end soon because it’s a lucrative full-time job for hackers. “They’re not wearing hoodies, sitting in grandma's basement hacking,” says Gates. “These guys drive Mercedes, have private jets, wear Armani suits, and basically are living a wonderful lucrative life by being criminals. How are you going to change that?”
The Bot Armageddon
If massive credit card thefts and epidemics of ransomware aren’t frightening enough, Gates foresees another threat on the horizon: The invasion of the botnets. Bots are small applications that automate tasks (such as a food ordering app for a restaurant). Hackers can turn internet-enabled devices, such as baby monitors, thermostats, cameras, or smartphones into bot networks. “Now the bots will attack on the instruction of the bot master,” explains Gates. A bot’s goal is to tumble passwords or spread ransomware. Using mass amounts of devices can amplify the power of the attack.
“It’s one attack with a hundred thousand or a million devices hacking simultaneously,” warns Gates. And it’s looming. “This bot problem is going to be out of control within the next three or four years.”
Cyber Security: More than a Threat
Despite a deep threat landscape, a strong element of naivety persists in the world. As Herman says, you don’t heed the hurricane warnings if you’ve never lived through a hurricane. Indeed, it’s not until you’re personally affected by a cyber security breach that you become more acutely aware of its potential. Herman explains that this mindset still exists among some smaller organizations - a sense of security by obscurity. He illustrates this sentiment: “We’re a small firm, nobody really knows about us. There’s not a big threat, so I’m not worried.”
In companies, CEOs and other C-level executives often set the tone to view security as an IT problem. When so many departments in an organization are networked and control sensitive data, cyber security becomes the entire team’s responsibility.
In addition to the mayhem and disruption that breaches and denial of service attacks cause, organizations may be held accountable for cyber security - especially if it’s a company that stores data or works with a business’ sensitive information. If the company has not enacted strong cyber security systems, auditors may sanction them, making it difficult to retain or attract new business. If your organization functions in a highly regulated industry, such as banking or healthcare, you may be subject to severe sanctions and penalties for data breaches. When dealing with countries outside the U.S., there may be specific times for reporting breaches.
What Systems Are at Risk of Cyber Security Attack?
We live in a computer-operated, networked world, and as such almost every aspect of our lives can potentially be affected by a cyber attack. Below is a list of some common security breaches that you should be wary of:
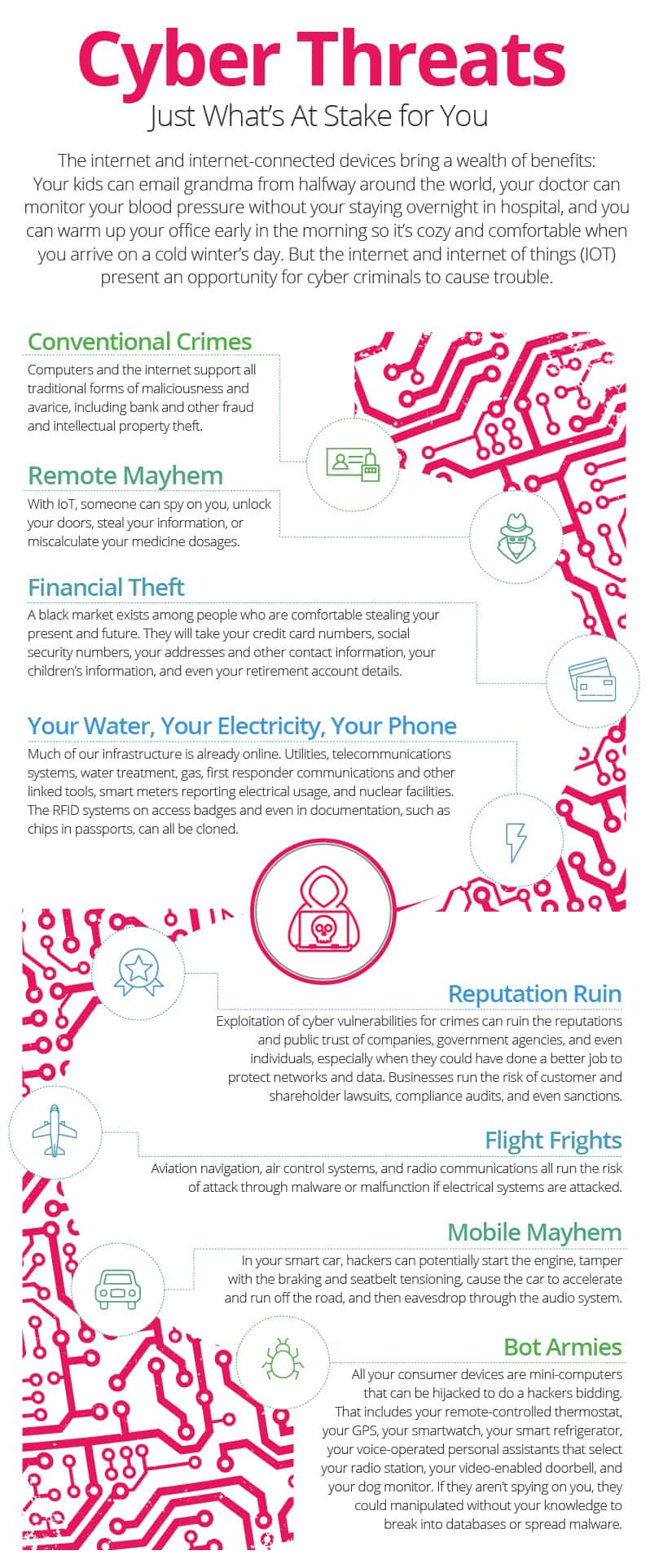
- Conventional Crimes: Computers and the internet support all traditional forms of maliciousness and avarice, including bank and other fraud and intellectual property theft.
- Remote Mayhem: With IoT, someone can spy on you, unlock your doors, steal your information, or miscalculate your medicine dosages.
- Financial Theft: A black market exists among people who are comfortable stealing your present and future. They will take your credit card numbers, social security numbers, your addresses and other contact information, your children’s information, and even your retirement account details.
- Your Water, Your Electricity, Your Phone: Much of our infrastructure is already online. Utilities, telecommunications systems, water treatment, gas, first responder communications and other linked tools, smart meters reporting electrical usage, and nuclear facilities. Imagine if every street light at an intersection in your town simultaneously turned to red - how would that affect traffic? The RFID systems on access badges and even in documentation, such as chips in passports, can all be cloned.
- Reputation Ruin: Exploitation of cyber vulnerabilities for crimes can ruin the reputations and public trust of companies, government agencies, and even individuals, especially when they could have done a better job to protect networks and data. Businesses run the risk of customer and shareholder lawsuits, compliance audits, and even sanctions.
- Flight Frights: Aviation navigation, air control systems, and radio communications all run the risk of attack through malware or malfunction if electrical systems are attacked.
- Mobile Mayhem: In your smart car, hackers can potentially start the engine, tamper with the braking and seatbelt tensioning, cause the car to accelerate and run off the road, and then eavesdrop through the audio system.
- Bot Armies: All your consumer devices are mini-computers that can be hijacked to do a hackers bidding. That includes your remote-controlled thermostat, your GPS, your smartwatch, your smart refrigerator, your voice-operated personal assistants that select your radio station, your video-enabled doorbell, and your dog monitor. If they aren’t spying on you, they could manipulated without your knowledge to break into databases or spread malware.
Governmental Agencies Concerned With Cyber Attacks
In the U.S., the Computer Fraud and Abuse Act and the Cybersecurity Act of 2015 is the law that officially prohibits misuse of computers and online fraud. In May of 2017, the White House released a Presidential Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure. Many governmental organizations within the U.S. deal with cyber security although, as David Herman suggests, the efforts can seem disparate. “There’s not just this one, plain English, public speaking list of here’s the things to do,” he says. “If you do searches, you’ll find government resources about vulnerabilities and things to do, but I think that the government hasn’t done a good job of consolidating it in a way that is approachable for most people.”
Stephen Gates echoes Herman’s sentiment that the government isn’t making a concerted effort. “Everybody’s sort of talking about it, but not really moving forward with anything,” Gates says.
These are some of the government agencies who focus on devices, networks, and cyber crime:
- Department of Homeland Security: National Cyber Security Division
- FBI, National White Collar Crime Center, Internet Crime Complaint Center, IC3 (where private citizens and companies report ID theft and other breaches)
- United States Department of Justice
- United States Cyber Command of the US Strategic Command
- Federal Communications Commission (FCC)
- Food and Drug Administration (FDA)
- US-CERT, the United States Computer Emergency Readiness Team (operates the National Cyber Awareness System with alerts primarily intended for computer experts)
- The U.S. Department of Energy, Office of Electricity Delivery and Energy Reliability
Computer crime is borderless and nationless and it can appear to happen here, there, everywhere, and nowhere, with source points and affected locations changing at the drop of a coin. Assigning local police to handle these incidents can be difficult. Cyber Emergency Response Teams (CERTs) exist in many other countries to watch for threats, but there are few uniform international laws or extradition treaties. Wherever cybercriminals are found, often the local law is not strong enough to bring the accused to trial, let alone justice.
Civilian Efforts Against Cyber Threats
Newly-hatched in early 2017, the not-for-profit Cyber Threat Alliance (CTA), aims to improve intelligence sharing for companies involved in cyber security, to protect the internet from hacking, and to prevent exploiting software. Founding groups include major software and cyber security companies including Cisco, Intel, Symantec, Palo Alto Networks, Fortinet, and Check Point Software Technologies, with former special assistant and cyber security advisor to President Barack Obama, Michael Daniel as its President.
How Are Systems Attacked?
Even a few years ago, a computer security event usually involved unauthorized access to a facility or a laptop unintentionally left in a taxi. Now threats come from the outside:
- Vulnerabilities: Weaknesses that exist in the design of software, its implementation, or the installation of equipment. These weaknesses become exploits in the hands of attackers who leverage vulnerabilities for malign purposes. Although one or several individuals may benefit from cyber attacks, probing for vulnerabilities itself is usually automated.
- Backdoors: A way into a system or program that circumvents the authorization process. Backdoors may be included intentionally for maintenance.
- Denial of Service Attacks: This type of attack renders computers or networks inaccessible to users. Forms of attack include repeatedly mangling an individual’s password so they are locked out of a system or overloading a system so it cannot respond. A distributed denial of service attack comes from multiple IP addresses, making it more complicated for a firewall to shut out malign calls and allow in legitimate users.
- Direct-access Attacks: Attackers may gain unauthorized access to a laptop to add malware, but attacks can also spread through other devices. Camcorders and storage devices, for example, directly access computer memory for high-speed transfers, which make them vectors for worms, keyloggers, and other malware.
- Eavesdropping: The surreptitious conversation monitoring, whether by listening in on a room, tapping into a landline or cell phone, or intercepting an email.
- Spoofing: The act of pretending to be something or someone you are not in order to gain access to sensitive information. You can spoof people or equipment, such as spoofing email addresses to distribute spam or spoofing caller IDs on VoIP networks.
- Tampering: The act of modifying devices, such as installing surveillance capability on a router or installing a rootkit, with software that permits access to parts of a computer that are usually inaccessible.
- Privilege Escalation: A user with some privileges can give themselves heightened privileges, including potentially superuser access to the entire system.
- Phishing: This is an attempt to acquire sensitive information by pretending to represent a legitimate organization or person, often someone of authority. Culprits send instant messages and emails to a swath of victims in the hope that some will bite.
- Ransomware: A method that locks data systems or individual devices. Ransomware may be installed through a phishing scam.
- Clickjacking: Through hijacking webpage links or user clicks, clickjacking redirects a user to a page that spoofs a legitimate page, often to collect sensitive information.
- Social Engineering: A sophisticated elevation of phishing wherein attackers use web pages, email, and even phone calls to pose as authority figures or friendly agents to acquire sensitive personal or company data. Social engineering often involves research on an individual through social media so that they can leverage the victim’s lifestyle, work, and interests. Examples can include an email under the name of a CFO asking for HR records, or a message requesting money from a “grandchild.” Other examples include emailing invoices under the guise of a legitimate vendor in order to secure payment into the accounts of thieves.
- Botnet: A network of private computers, including portable devices that are surreptitiously controlled as a group to propagate spam or break passwords.
What Is A Cyber Policy?
A cyber policy is relevant at many levels in our society. On a national level, cyber policy governs how we approach questions of data privacy, personal privacy, freedom of speech, security, access to the internet, and commodification of the internet. On a local or private level, an organization’s cyber policy guides how employees, contractors, and visitors use its computers and network assets. The policy precisely describes those assets, appropriate and acceptable use, potential threats against the devices and network, and how the organization will defend against threats, contain and repel threats, and repair any damage.
Several government agencies concerned with cyber security offer useful policy tools. The FCC’s online Cyber Planner helps you build a template for the particular needs of your organization’s cyber plan. The FCC also provides a background guide, the FCC Small Biz Cyber Planning Guide, with 45-pages of advice on computer security training, facility security, and links to publications and pertinent government agencies. Another resource from the Financial Industry Regulatory Authority (FINRA) is the Excel-based Small Firm Cybersecurity Checklist.
The National Institute of Standards and Technology (NIST) offers a Cyber Incident Response Plan, which includes a detailed guide and a one-page checklist for preparing for major security incidents.
Cyber Security Frameworks
At a high level, federal agencies and non-governmental organizations (NGOs) create policy frameworks to describe best practices for cyber management and cyber security, and to guide organizations in compliance with regulations.
- NIST Framework: The NIST Framework for Improving Critical Infrastructure Cybersecurity describes activities grouped around five core functions - identify, detect, protect, respond, and recover - to promote cybersecurity. The NIST framework draws from other frameworks and standards, including ISO 27000, Information Technology Security, and ISO 31000 Risk Management. The NIST framework is also available as an Excel document.
- ISO/IEC 27000: The ISO 27000 series of standards governs information security.
- COBIT: Control Objectives for Information and Related Technology, created by the Information Systems Audit and Control Association, known by its acronym, ISACA, provides a framework for management and governance of enterprise information technology. Its specifications demonstrate compliance with data and IT components of Sarbanes Oxley.
- SSAE-16: The Statement on Standards for Attestation Engagements (SSAE)-16 provides a framework for allowing companies to communicate their cyber security effectiveness with certified public accountant auditors and others.
While frameworks describe a theoretical model for the types of things an organization should include in a cyber policy, growth and improvement are described through a cyber security maturity model. A cyber security maturity model document provides a view into the level of sophistication of an organization’s approach to cyber security and provides a roadmap for enhancement.
Even IT security professionals can find frameworks daunting reading (the NIST Cybersecurity framework is 66 pages). If your company is subject to compliance audits, security consultants suggest leveraging managed security services. Doing so may remove considerable effort and worry from your shoulders as you attempt to secure and prove security for your establishment.
Cyber Security Disasters and What We Can Learn from Them
Sadly, revelations of data breaches or serious intrusion attempts seem to be a weekly, if not daily, occurrence. Examples of notable hacks focusing on assorted targets include the following:
- Robert Morris and the First Computer Worm: One of the world’s first computer worms was hatched in 1988 by a Cornell University graduate student, Robert Morris. With only around 50,000 plus workstations and mainframes in existence at the time, the problem revealed itself one day, November 2. Computer processes slowed while the worm clogged devices with multiple processes and copied itself to other devices. The result of the attack was the impetus to create CERT, Computer Emergency Readiness Team, at MIT.
- Rome Laboratory: In 1994, two hackers (both under the age of 25 at the time) used a sniffer program to gain access to a U.S. Air Force R&D facility Deploying Trojan Horses. Masquerading as Roma employees in order to cover their tracks, the hackers were able to deploy over a hundred intrusions into the facility to steal data. During the attack, the Trojan Horses also gained access to other networked facilities in the U.S. Department of Defense (DoD) and civilian computers.
- Target and Home Depot: Between 2013 and 2014, a vulnerability in point-of-sale devices at the two stores provided a way for hackers to steal customer credit card data. Home Depot had allegedly received warnings about a possible attack that could have been prevented by installing antivirus upgrades.
A Cybersecurity Ventures 2016 report estimates the costs of hacks to banks, corporations, and individual victims at as much as six trillion within a few years. Cybercrime prevention itself is a growing business, an IDC report estimates the worldwide security technology market will surpass $100 billion by 2020.
Why Do People Hack?
In the beginning, hackers often broke into systems and stole data for the thrill of it. Often, they claimed they were searching for evidence of conspiracies, and to show weaknesses in system security. Hackers sometimes work for local, national, or international interests. Today, people hack mainly because of avarice: Stealing credit card numbers, social security numbers, and holding networks ransome pays.
Why people choose to hack, what they want, and how they will attack is studied through threat modelling. Security analysts in an organization study the software an organization uses to evaluate threat points, and also record the specifics of actual security events and how they were mitigated so the organization can improve cyber security defenses.
To combat cyber crime, we simply need to toughen up. As Gates urges,“We have to make it so difficult and time consuming, and they’ll [hackers] eventually see that it took them a 1,000 hours to make 10 dollars.”
That may actually be easier than it sounds. The majority of successful attacks result not from exploiting unknown vulnerabilities, known as zero-day events, but by taking advantage of known problems that remain unpatched. In fact, as the Department of Homeland Security reported, eighty percent of attacks leverage known vulnerabilities and configuration management setting weaknesses.
Tips to Promote Cyber Security
Take comfort in the fact that most successful attacks leverage known vulnerabilities that you can easily eliminate with patches, up-to-date infrastructure (such as firewalls and other equipment), and good configuration management. Beyond good IT practices, however, organizations also must foster an information security culture. Employees can easily think of cyber security as the purview of management and the IT department. In fact, management and IT need to lead their team members in taking responsibility for cyber hygiene.
As individuals, we have to protect ourselves. “Assume your information has been stolen, and now you’ve just got to have your guard up,” advises Gates. Part of that includes regularly monitoring your credit report.
He also stresses the importance of implementing 2FA, or two-factor identification, for every online account that offers it. With two-factor identification, you access a web application or even a device, with not only a username and password, but also with a third separate piece of information (usually a code sent to an email account or phone), which you enter to gain access. This added layer of protection helps in cases of stolen usernames; thieves still cannot get into your account. “2FA makes a lot of sense for every single consumer,” says Gates.
You can prevent many intrusions, breaches, and the spread of malware simply by guarding how you handle email and act on nefarious requests. Below are some situations you might encounter and tips on how to handle them.
- A terse email appears from the address of someone you recognize, your cousin or your boss, with a generic link such as, “Look at this video.” Don’t look at this video, delete the email.
- Someone who says they’re a recruiter informs you via email that they have the perfect opening for you. Then they ask to meet on Google hangouts, and their email address is a Hotmail account. They ask for sensitive information, like your social security number, through email, and inform you that $200 will start the hiring process for you. Run away!
- The site administrator at your bank sends you a message requesting that you send them your password. No you don’t!
- Your CFO just asked for information on everyone in your company’s payroll. There are safer ways to share sensitive information within your company. Remember, if something seems questionable, pick-up the phone to verify the request. The CFO probably has other ways of accessing that data.
- You receive a random email request from your bank, the IRS, your company administering your retirement plan, the Social Security Administration, or any other institution, offering you a link to their “website” and asking for personal information. Before responding, type the web address of the institution into your browser to verify that the source is legitimate before clicking on the link. These institutions typically send actual mail for these requests.
- If you work in the accounts payable department and receive an email from a known vendor directing you to pay them on their new site, think twice and verify with the vendor before you transfer.
Practical Cyber Security Tips You Can Implement Now
Although the risks of unsecured devices and networks are daunting, implementing strong security practices doesn’t have to be.
- Install Patches: Software updates aren’t pushed out just to share cool new features. Patches close vulnerabilities. “Over the years, I’ve seen company after company and person after person not taking advantage of updates,” says Herman. “That makes a difference. Updates shut down a lot of bugs.” That holds true for updating system software on cell phones, too. Herman advises, “We should leverage the free tools they provide us to close threats down ourselves.”
- Practice Password Discipline: Password security is no longer derived from complexity, but from length. If you need to remember many long passwords, use a locker tool.
- Leverage Traditional and New Antivirus Software: Schedule deep scans and when in doubt, use quick scans.
- Educate the Team: “There’s a huge human element to risk associated with cyber security,” Herman says. Through education comes a heightened vigilance. Use experts to help your employees become “cyber defense warriors.”
- Consider Managed Services: Rather than maintaining your own servers, including patches and hardware, consider cloud-based work platforms, storage options, file-sharing, and cyber threat protection. Managed well, cloud-based protection systems offer around-the-cloud monitoring for your network infrastructure, and also regularly investigate new threats and implement solutions.
- Keep Cyber Security Resources at Hand: Herman suggests having a resource on speed dial so that you can reach out the moment you suspect a breach.
- Promote a Culture of Forgiveness: Companies must cultivate an environment that encourages honesty with regards to cyber security problems. “If you click on a wrong link, be open and honest about it before it causes damage for the whole team,” advises Herman. And, don’t be afraid to shut down that device the moment you suspect something might be wrong.
Practical Aspects of Cyber Security
In addition to developing and distributing a cyber security policy, there are plenty of things you can do to start protecting your digital work assets:
- Protect physical access
- Create an information security culture
- Protect your network and equipment from injections and intrusions
- Work by the following principles: Security by design, unit testing, principle of least privilege, defense in depth, audit trails, and full disclosure
- An intact system can be described by its confidentiality, integrity, and availability. Security architecture describes how defense and countermeasures are situated to ensure system solidity. Some of these efforts that also play a role in network security include the following:
- Firewalls
- Intrusion detection (machine learning for persistent threats)
- System access controls (reduces vulnerabilities, also 2FA, backups)
- Cryptography
- Detection response
- Vulnerability management
- Access control
- Hardware protection: Dongles, drive locks, disable USB ports, AES, thumbprint and other biometric, BlueTooth near field detection
- Access-control list versus capability based security
Improving Cyber Security in Healthcare Organizations
As healthcare companies begin to leverage more technology resources to house their data, the threat of cyber attacks continues to be a growing problem. Cybersecurity methods are becoming more necessary to secure devices, networks, data, and information.
This is particularly important for healthcare organizations, which must remain HIPAA compliant and ensure that all personal health information (PHI) and other confidential information is secure and protected within their systems. Additionally, patient information and medical processes and procedures, if threatened or hacked, could result in life-threatening situations if any information is altered or deleted, meaning data must always remain protected.
To combat the growing issue of cyberattacks and improve the security of computer systems and critical data, healthcare companies need a powerful, real-time, and secure tool that will ensure the protection and safety of all information and processes.
Smartsheet is a work execution platform that enables healthcare companies to improve data safety, manage security processes, and keep privacy in check. Securely track and share confidential information with authorized users, mange control of user access, and increase visibility into who has access to what business-critical information, while meeting or exceeding all of HIPAA’s regulatory requirements. Rest assured that all of your valuable assets are encrypted and stored under strict security infrastructure, eliminating the threat of cyberattacks and data loss.
Interested in learning more about how Smartsheet can help you maximize your efforts? Discover Smartsheet for Healthcare.
Talent Shortage and Training in Cyber Security
Some estimates suggest that over a million openings in cyber security exist, and that openings will triple by 2019. How can positions go unfilled when information technology so permeates our modern world?
Some articles emphasize that the approach to cyber security recruitment must change. Rather than viewing computer security as a silo within information technology, employers and job placement professionals should view it as a complementary endeavor. Organizations should consider leveraging the talents and skills of existing employees and supporting their ongoing training in cyber security. Companies may also improve their outreach to high schools and universities to encourage students to consider cyber security as a career path.
Gates suggests that much of the talent shortage can be mitigated through machine learning, a step on the path to artificial intelligence (AI). In machine learning, computers analyze data to determine patterns faster than humans can. Some cities, for example, already employ machine learning to monitor hundreds of street lights, parking meters, and cameras. In human-assisted machine learning, a person then corrects and guides the computer until the computer can recognize threats and anomalies on its own. “A machine can learn to detect things that it’s never seen before,” says Gates.
Training
Cyber security training is heavily represented through paid online cyber security degrees, often from Ivy League institutions, and also through massive open online courses (MOOCs). Courses are available in English, Italian, and Korean.
Curricula cover the spectrum of concerns, with cyber security for critical infrastructure, aviation, cryptocurrencies, IoT, information security, homeland security, domestic and foreign political considerations, in addition to hardware and programming topics.
- Potential cyber security students may consider qualifying for the CISSIP or Certified Information Systems Security Professional certificate. This coveted certification trains and tests candidates in the 10 security domains:
- Access Control Systems and Methodology
- Telecommunications and Network Security
- Business Continuity Planning and Disaster Recovery Planning
- Security Management Practices
- Security Architecture and Models
- Law, Investigation, and Ethics
- Application and Systems Development Security
- Cryptography
- Computer Operations Security
- Physical Security
Roles
As the world is increasingly digitized and networked, organizations of all sizes and types will require computer security as an essential part of everyday business. Salaries for cyber security professionals compensate for the responsibility and intensive training involved. For example, the median salary for an information security officer is $90,000. Cyber security professionals can use their skills in a variety of roles:
- Security analyst
- Security engineer
- Security architect
- Forensics investigator
- Cybersecurity specialist
- Security consultant/specialist/intelligence
Improve Cyber Security with Smartsheet for IT & Ops
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.