Enterprise Risk Management Frameworks
Enterprise risk management frameworks relay crucial risk management principles. You can use an ERM framework as a communication tool for identifying, analyzing, responding to, and controlling internal and external risks. An ERM framework provides structured feedback and guidance to business units, executive management, and board members implementing and managing ERM programs.
ERM frameworks help establish a consistent risk management culture, regardless of employee turnover or industry standards. They guide risk management functions and help enterprises manage complexity, visualize risk, assign ownership, and define responsibility for assessing and monitoring risk controls. A custom ERM framework supports the enterprise in integrating risk management into significant business activities and functions.
Types of Enterprise Risk Management Framework
The strategic framework you choose will depend on your industry, business goals, organizational structure, technology infrastructure, and available resources. Some frameworks are more applicable to enterprise-scale businesses, while others provide more customizable, scenario-based approaches to an organization's specific ERM needs.
There is also a subset of strategic enterprise risk management frameworks — for example, some may better fit the needs of highly regulated industries like finance and healthcare. You can use any of these as a starting point to build a custom ERM framework.
The Casualty Actuarial Society (CAS) ERM Framework
The Casualty Actuarial Society (CAS) is an international credentialing and professional education entity. The organization focuses exclusively on property and casualty risks in insurance, reinsurance, finance, and enterprise risk management.
The CAS, Society of Actuaries (SOA), and Canadian Institute of Actuaries (CIA) sponsor a risk management website with ERM education resources. The committee organizes the ERM framework by risk type and a sequential risk management process.
The four risk types are defined as follows:
- Hazard Risks: This category contains liability suits, property damage, natural disasters, crime, work-related injuries, and business interruption.
- Financial Risks: This category contains price risk, liquidity risk, credit risk, inflation risk, and hedging risk.
- Operational Risks: This category contains operational risk, empowerment risk, IT risk, integrity risk, and business reporting risk.
- Strategic Risks: This category includes competition, customer risk, demographic and cultural risk, innovation risk, capital availability, regulation, and political risk.
The CAS risk management process involves the following seven sequential steps:
- Establishing Context: The first step is setting the context for risk based on how the organization currently operates. This step includes understanding internal and external context and ERM context (for example, danger to specific business units and the organization's environmental risk).
- Identifying Risks: Document threats that prevent your organization from achieving its business objectives. This stage also encourages you to define how you might take advantage of risk to obtain a competitive advantage.
- Analyzing Risks: In this step, analyze risk probability outcomes for each risk and quantify the impact.
- Integrating Risks: In this step, aggregate risk distributions, considering correlations and the effects of risk on portfolios. Measure this stage by the impact to key performance indicators (KPIs).
- Prioritizing Risks: Assess and prioritize each risk to determine how it adds to the aggregate ERM profile.
- Exploiting Risks: This step requires developing strategies for using various risks to the organization's advantage.
- Monitoring Risks: The last step focuses on performing continuous reviews of the risk environment and overall ERM performance.
The steps in the risk management process might apply to each risk individually. The checklist below is based on the committee's ERM framework grid in the aggregate.
The COSO ERM Integrated Framework
In 2017, COSO published an updated ERM framework, Enterprise Risk Management—Integrating with Strategy and Performance, to address the importance of ERM in strategic enterprise planning and performance. This updated model accounts for the increased complexity of modern business environments.
The Committee of Sponsoring Organizations of the Treadway Commission (COSO) is a joint initiative of five private-sector organizations dedicated to offering thought leadership by cultivating comprehensive frameworks and guidance on enterprise risk management, internal control, and fraud deterrence. Below are the organizations that sponsor and fund the COSO private sector initiative:
- American Accounting Association
- American Institute of Certified Public Accountants
- Financial Executives International
- Institute of Management Accountants
- The Institute of Internal Auditors
COSO incorporated the Sarbanes-Oxley Act (SOX) legislation for risk management guidelines into its ERM framework. This integration made the COSO framework popular with large corporations, banks, and financial institutions subject to extensive legal codes and high-risk business.
5 Interrelated Components of COSO ERM Framework
The updated COSO framework includes five interrelated enterprise risk management components. These components include 20 principles that cover practices from governance to monitoring, regardless of enterprise scale, industry, or type of organization.
The following components of the widely-used ERM framework fits business models, not independent risk management processes:
- Governance and Culture: This component incorporates five principles, including board risk and oversight, operating structures, defining culture, core values commitment, and human resources practices for recruiting, developing, and retaining individuals.
- Strategy and Objective-Setting: This component covers four principles: analyzing business context, defining risk appetite, alternative strategies, and business objectives.
- Performance: This component contains five principles, including risk identification, assessing risk severity, risk priority, risk response implementation, and portfolio development.
- Review and Revision: This component addresses three principles: substantial change assessment, risk and performance reviews, and pursuing ERM improvement.
- Information, Communication, and Reporting: This section includes leveraging IT, risk communication, and reporting on risk culture and performance.
The following table summarizes the updated COSO ERM Framework control components and principles.
The ISO 31000 ERM Framework
The International Organization for Standardization (ISO) 31000:2018 ERM framework is a cyclical risk management process that incorporates integrating, designing, implementing, evaluating, and improving the ERM process.
The ISO 31000 model is reviewed every five years to account for market evolution and changes to business complexity. This framework covers various risks and is customizable for organizations, regardless of size, industry, or sector. To learn more about this model and download free templates and matrixes, read “ISO 31000: Matrixes, Checklists, Registers and Templates.”
The ISO/IEC 27001 ERM Model
The ISO/IEC 27001 security standard provides requirements for information security management systems (ISMS). More than a dozen security standards provide physical and technical information risk management controls for ERM programs. Digital enterprises in various industries adopt ISO 27001 to manage financial, intellectual property, and internal data security.
The COBIT ERM Framework
COBIT (2019) is a flexible IT governance and management framework created by the Information Systems Audit and Control Association (ISACA). The conceptual framework is a popular choice for managing risk in a digitized enterprise environment.
COBIT provides a risk management model for large enterprise business capabilities and a model to fit specific areas of small to medium enterprises. Managing information and technology risk is no longer limited to the IT department, due to the integration of IT in every aspect of modern business operations.
“We look at COBIT and COSO at the top down level as we're putting together our program,” says Michael Fraser, CEO and Chief Architect at Refactr, a Seattle-based startup that provides a DevSecOps automation platform that offers IT-as-code services and DevOps-friendly features made for cybersecurity. “We're also looking at how those map to every control that we looked at in those frameworks. Is that something that we can automate internally? Is it something that requires a manual process? We build that content for our customers and check to make sure that this is a dynamic program that works for us and for the customer,” he says.
COBIT is a flexible umbrella framework for creating an ERM framework with processes that align business and IT goals to prevent risk management silos across an enterprise. The framework identifies the following three core principles for building a governance and management framework:
- Conceptual: A governance framework should identify critical components and their relationships to maximize consistency and empower automation.
- Agile: A governance framework should be open and flexible to new content and address issues that arise with agility, integrity, and consistency.
- Aligned: A governance framework should align with different standards, other frameworks, and regulatory requirements.
There are also six core requirements for an enterprise IT governance system that an organization can adapt and design to fit an ERM framework:
- Valuable: It should satisfy stakeholders across board members, executive leadership, and management.
- Holistic: The ERM framework is built from components that work together for a comprehensive approach to risk management and governance.
- Dynamic: The framework should react to changes to the ERM program's design factors and consider the impact of each change.
- Distinct: The framework should clearly distinguish management and governance activities.
- Customized: The framework should be tailor-made using design factors to optimize risk management and governance.
- Comprehensive: The framework should provide end-to-end ERM coverage for IT functions and all information and technology processing across the enterprise.
The NIST ERM Framework
The National Institute of Standards and Technology (NIST) is a U.S. federal government agency (U.S. Department of Commerce). The NIST framework is a cybersecurity framework used by private enterprises doing business with the U.S. government agencies, such as the Department of Defense (DoD).
The NIST framework model focuses on using business drivers to guide cybersecurity activities and risk management with three components:
- Framework Core: This is a set of five cybersecurity outcomes, with subcategories, activities, and informative references common to most business sectors and critical IT infrastructure.
- Identify: Asset management, business environment, governance, risk assessment, and risk management strategy
- Protect: Identity management, access control, data security, protective technology, and maintenance
- Detect: Anomalies and events, detection processes, and continuous monitoring
- Respond: Response planning, communications, analysis, mitigation, and improvements
- Recover: Recovery planning, improvements, and communications
- Implementation Tiers: This is a mechanism to help organizations prioritize and achieve cybersecurity objectives to manage cybersecurity risk.
- Framework Profiles: Here, use the framework core elements to help develop organizational profiles and align cybersecurity activities with the mission, risk tolerance, and available resources.
The NIST framework provides a globally recognized standard for cybersecurity guidelines and best practices that apply to enterprise-scale organizations with critical infrastructure to protect. The framework is a flexible model for creating an ERM framework for organizations that rely on technology, are concerned with data privacy, and that manage risk associated with the latest digital workforce trends.
"The Center for Internet Security maps a lot of its framework or benchmarks to NIST and ISO and maps those to an ERM framework,” explains Fraser. “Everything is interconnected because you're trying to mitigate risk. You're also trying to check boxes for a particular scenario — whether that's for an audit or for a customer that wants us to practice due diligence to meet their risk management standards.”
RIMS Risk Maturity Model ERM Framework
The nonprofit risk management society (RIMS) Risk Maturity Model (RMM) assessment consists of 68 readiness indicators that describe 25 competency drivers for seven critical ERM attributes to benchmark organizations against industry peers, track progress, and help execute an action plan.
7 Attributes of RIMS ERM Framework
The RIMS RMM framework identifies the following seven key attributes of ERM competency:
- ERM-Based Approach: This attribute focuses on enterprise risk culture and degree of commitment from executive leadership and board members for adopting an ERM-based approach.
- ERM Process Management: This attribute concentrates on organizational culture and the level of integration across critical business processes for explicit, repeatable ERM processes.
- Risk Appetite Management: This attribute centers on leadership accountability and the level of decision-making awareness concerning risk tolerance and gaps between perceived and actual risks.
- Root Cause Discipline: This attribute emphasizes the search for the root causes of each risk, including risk classification, uncovering risk outcomes, linking to sources, and improving risk response and controls.
- Uncovering Risks: This attribute concerns scoping risk assessment, analyzing information sources, and documenting risks and opportunities.
- Performance Management: This attribute focuses on ERM vision, mission, and strategy, including goal planning, communication, execution, and measurement using quantitative and qualitative KPIs.
- Business Resiliency and Sustainability: This attribute assesses ERM information used for operational planning, disaster recovery planning, and other scenario analyses.
Evaluate each attribute using a scale of five maturity levels: nonexistent, ad hoc (level one), initial (level two), repeatable (level three), managed (level four), and leadership (level five). The RIMS RMM framework is a flexible model that is compatible with customized ERM frameworks based on the international ISO 31000:2018 standard, the updated COSO ERM framework, or the COBIT framework.
The Case for Custom ERM Frameworks
“There's not a one-size-fits-all framework, and you’ll start realizing you need something different,” says Michael Fraser of Refactr. “That's what we found at Refactr, but we're unique because we help organizations create the automation that they want to use to help them with these particular frameworks.”
“The risk management frameworks out there are guides to help you understand what you need to do in a standardized way,” Fraser continues. “So, there's something universal that you can work with that other people understand. They [the standard frameworks] are there to help you build your security program and not there to be this bar you never reach.”
Fraser advises asking if the framework is good enough for your organization to do business with your target customers. The most critical piece of advice comes down to the why — i.e., “Why do you need an enterprise risk management framework?”
“A lot of these risk frameworks are antiquated in what they talk about,” he says. “With more people working from home, you don't necessarily have the corporate networks. What if you're born in the cloud or a 100 percent remote, cloud-native company?”
Objective Setting for Strategic ERM Frameworks
“Risk management is the overarching discipline in cybersecurity, and the focus tends to be on the technology aspects. But, for the enterprise, it's how to attract and retain profitable clients,” explains Sean Cordero, an Advisor to Refactr. “One of the things that gets lost for some organizations is the explosion of cloud-delivered services. Cloud architecture enables a way of doing things now that has little to no relevance to the way things were done.”
Cordero advises addressing some difficult questions before creating a custom risk framework. Ask the following questions: Is anyone going to use this ERM framework? Is it going to help move the needle from an industry perspective? Take a step back and assess what the risk is and what matters, using three simple inputs to prioritize strategic risk management, before implementing a custom ERM framework.
“First, look at what is required by the law. Second, identify what your customers are going to need, which will depend on the type of organization,” says Cordero. “If you're maintaining sensitive data for your customers and they care about that sensitive data, focus on the confidentiality aspects, whether that's encryption or a multitude of ways to get there. Finally, determine what you value as an organization. What are you okay with when considering your clients and your business? This is a very introspective thing that is sometimes missed. If you do it, you will suss out clearly where to focus and can then select the appropriate risk management framework or approach.”
How To Develop a Custom Enterprise Risk Management Framework
Developing a custom ERM framework helps implement a risk management strategy, align business objectives, and promote risk-based decision-making. But, customizing an ERM framework to fit internal objectives, customer needs, industry regulations, IT governance, and internal audit standards doesn't have to be overwhelming.
The following roadmap for developing a custom ERM framework is based on existing management and operational risk frameworks, ERM models, and input from industry experts. Use this step-by-step process to develop and implement a custom ERM program. To learn more about ERM implementation, see our “Guide to Enterprise Risk Management Implementation.”
ERM Framework Stage One: Build a Cross-Functional ERM Team
Select stakeholders across different business units and management for the ERM steering committee. The overall effectiveness of a custom ERM framework depends on support from all management levels, particularly executive leadership, senior management, and the board of directors.
Build a cross-functional ERM team to drive buy-in at various operational levels and impact the culture. The ERM team sets business objectives, and develops a risk profile and a risk appetite statement (RAS) based on the threats and opportunities within their expertise.
Stage One Questions:
- Who should be included in creating the risk governance structure?
- What roles and responsibilities will you assign to each stakeholder on the risk committee?
- Are the roles and responsibilities clearly defined (with descriptions)?
- Is the development of the ERM framework independent of specific business functions, or does it favor operational influence areas?
- Do we need to establish a separate risk management oversight committee for checks and balances?
ERM Framework Stage Two: Identify Risk
Recognize and plan for risk events — internal and external threats and opportunities that create doubt and may affect business outcomes. Use your risk profile and RAS to align the business strategy with risk identification.
The ERM framework is the playbook for identifying and addressing risks that threaten business objectives. Use it as a guide to distinguish risk threats from risk opportunities that may lead to achieving desired outcomes. Map risk events back to objective setting activities in Stage One and identify internal and external risks. Be sure to include your customer's risk perspective, as well.
Leverage industry best practices and the ERM steering committee’s expertise to guide your analysis of future threats and opportunities.
Stage Two Questions:
- Are we identifying future risk, or is our focus too narrow on current threats and opportunities?
- Did we develop a repeatable methodology for identifying risk events with clear standards and procedures that leverage collective expertise?
- Did we identify risk opportunities that map to business strategy and help mitigate other threats?
- Can we accurately rank risk using parameters, such as probability and potential financial loss?
- Did the risk identification stage of framework development prioritize risk events for response and mitigation?
ERM Framework Stage Three: Evaluate Risk
Risk assessment sets the foundation for managing risk and determining its probability. This stage is the heavy analysis phase of framework development — in it, you will establish an integrated risk assessment framework.
Use risk assessment and compliance tools like a risk assessment matrix and risk control self-assessments (RCSAs) to plan the assessment methodology. Risk assessment forms are useful for evaluating risk and establishing risk controls, which is the core activity in Stage Four. To learn more about planning a custom risk assessment methodology, see our guide to enterprise risk assessment and analysis.
Stage Three Questions:
- Did we establish the problems and impact (financial, operational, internal, customer) for each potential risk event?
- Did the evaluation stage of framework development demonstrate a fact-based understanding of the enterprise risk and current ERM capabilities?
- Did we use risk assessment tools to identify gaps in the existing ERM capabilities and determine a path forward to addressing each?
- Did the risk assessment phase of development change how we rank and prioritize types of risk, based on Stage Two risk identification parameters?
ERM Framework Stage Four: Treat Risk
Treating risk is the action phase of an ERM framework. This stage involves designing and implementing the control environment and creating a risk mitigation action plan that covers how to respond to each type of risk event identified in previous stages.
Risk owners manage the control environment. Assign roles and responsibilities to risk owners to pinpoint when and how to respond. Determine which business units are affected by and responsible for specific risk controls.
Internal controls are specific actions that risk owners take to respond to threats or leverage opportunities. Align separate internal and external controls based on business objectives, customer requirements, industry legal and regulatory requirements, compliance standards, and governance structures.
ERM Framework Stages of Risk Response
The ERM framework helps you to address various stages of risk response and determine appropriate controls. Your response and mitigation strategy will vary by the type of risk, risk profile, and risk tolerance. The stages of risk response include the following:
- Accept: If it costs more to mitigate the risk, accept the risk and monitor the results.
- Avoid: This is the best response to threats with a high probability of financial loss or detrimental outcomes.
- Reduce: If the risk is likely to occur, but presents an opportunity that outweighs minimal financial loss or other factors, mitigate the threats with framework controls and monitor them.
- Share: Transfer risk that carries more significant threats and use insurance or third-party mitigation techniques to hedge against loss or problematic outcomes.
Stage Four Questions:
- Do our internal control environment and risk response and mitigation strategy have appropriate checks and balances that create accountability for risk owners?
- Do we have a policy and procedure in place to review risk controls and risk ownership?
- How often will we monitor and review controls and control ownership?
- Did we establish the appropriate response strategy and controls against our risk tolerance for specific types of events?
- Did we account for external vendor-controlled systems and partnerships with internal ownership and response controls?
ERM Framework Stage Five: Optimize Risk
Risk optimization is the final stage. The specific tools you need to optimize risk varies based on resources and overall objectives. Consult your ERM objectives to pick the set of analytics capabilities and reporting technology you need. These should not drive the type of ERM framework you develop.
Monitor and review ERM program performance in order to create a data-driven, objective feedback loop. This iterative loop flows across the enterprise at all levels and in all directions to optimize risk management. Then, use that data to identify areas of opportunity to revise and enhance the ERM program.
Leverage compliance audits that match best practices for your industry and governance requirements. Create a role-based, risk reporting dashboard to track and report on strategic risk objectives, control metrics, and KPIs. Modern ERM software platforms provide cloud-based dashboards with built-in business intelligence and user-friendly reporting features.
Stage Five Questions:
- Do our risk monitoring reports and ERM dashboards enable management to adjust to real-time risk environments?
- Did we incorporate IT and cybersecurity governance best practices to optimize security risks and determine if our ERM infrastructure complies with modern, cloud-based security standards?
- Does our ERM infrastructure and operations empower continuous risk monitoring, reporting, and communication using automation and continuous integration practices?
- What is our optimal cadence for reviewing and modifying our ERM framework, based on analysis of our risk response and overall risk environment?
- Does our custom framework empower risk awareness and transparency and break down risk silos?
Tools for Developing Custom ERM Framework Components
Creating a custom ERM framework involves leveraging risk management best practices, tools, and proven strategy. Incorporate the following risk management tools to develop custom ERM framework components that fit the enterprise’s — and the customer's — needs:
- Risk Appetite Statements (RAS): This documentation defines the key risk considerations for risk response and mitigation in aggregate, based on enterprise objectives and overall risk profile.
- Risk Tolerance Models: Your custom ERM framework should outline the level at which the enterprise can safely identify, control, and respond to threats and opportunities. For free downloadable risk assessment templates, see “Free Risk Assessment Form Templates and Samples.”
- Risk Reporting Dashboards: Risk management platforms have risk reporting dashboards. Design role-based dashboards based on the ERM steering committee members and responsibilities. Use ERM dashboards to monitor key risk indicators. To learn more about risk management software features and advantages, read “How to Choose the Right Risk Management Software.”
- Risk Data Analytics and KPIs: Use key risk indicators and metrics to monitor and determine risk thresholds and accountability. ERM dashboards are tools for monitoring and reporting risk metrics and KPIs.
- Internal Compliance Audits: Leverage RCSAs for each business unit to assess the effectiveness of internal controls and measure compliance standards. To learn more about compliance audits, see “Compliance Auditing 101: Types, Regulations and Processes.”
- Stochastic Risk Models: Model risk using this popular form of financial modeling in order to determine risk forecasts. The method also identifies the probability of uncertain threats and risk opportunities occurring at random.
- Risk Management Plan Templates: A risk management plan is a schematic within your ERM framework that helps specify your ERM approach. Use risk management plan templates like risk registers and a risk assessment matrix to create a custom ERM framework. To learn more about risk management plans and to find free downloadable templates, see “Free Risk Management Plan Templates.”
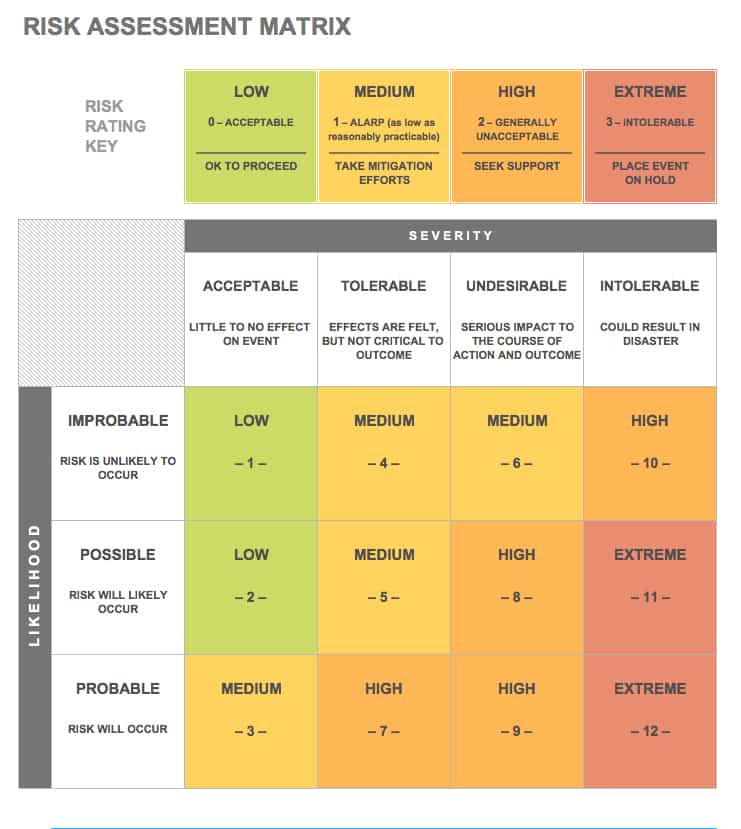
Risk Assessment Matrix Template
Download Risk Assessment Matrix
Microsoft Excel | Microsoft Word | Adobe PDF | Smartsheet
Use this risk assessment matrix template to get a quick overview of the relationship between risk probability and severity. The template’s simple color scheme distinguishes between different risk ratings.
Custom ERM Framework Criteria
James Lam outlines a set of standard criteria for his Continuous ERM Model in the book Implementing Enterprise Risk Management. He combines the components of well-known strategic management frameworks into a customizable communication framework with the following criteria:
- Simple: Lam recommends simplicity when determining ERM guiding principles. He uses the example of a roadmap, which is simple enough to follow but comprehensive enough to ensure you arrive at the desired location. Keep your framework components to seven or less, the optimal range for human memory.
- Mutually Exclusive, Collectively Exhaustive (MECE): A custom ERM framework should be unique to your business goals and resources. The components should stand alone without overlap or redundancy. That said, Lam recommends that parts be comprehensive enough to cover all levels of your enterprise and account for every outcome.
- Balanced and Integrated: The ERM framework needs to integrate with the entire enterprise organization and the risk management program context. Lam uses the example of an automobile engine to highlight his point. The framework shouldn’t overemphasize any one component but should remain balanced and in harmony, just like the engine and steering wheel of a vehicle.
- Flexible: The changing dynamics of an enterprise-scale business, as well as the rapid pace of technological innovation and industry change, make it vital for a custom ERM framework to be flexible. Lam suggests creating a framework template that embraces your organization’s long-term business goals while accounting for a risk's unknowable nature.
- Effective: Lam explains that the effectiveness of a framework depends on its implementation. Measure effectiveness by the integration of risk management into the decision-making process and enterprise business outcomes. To learn more about implementing ERM programs, see “Guide to Enterprise Risk Management Implementation.”
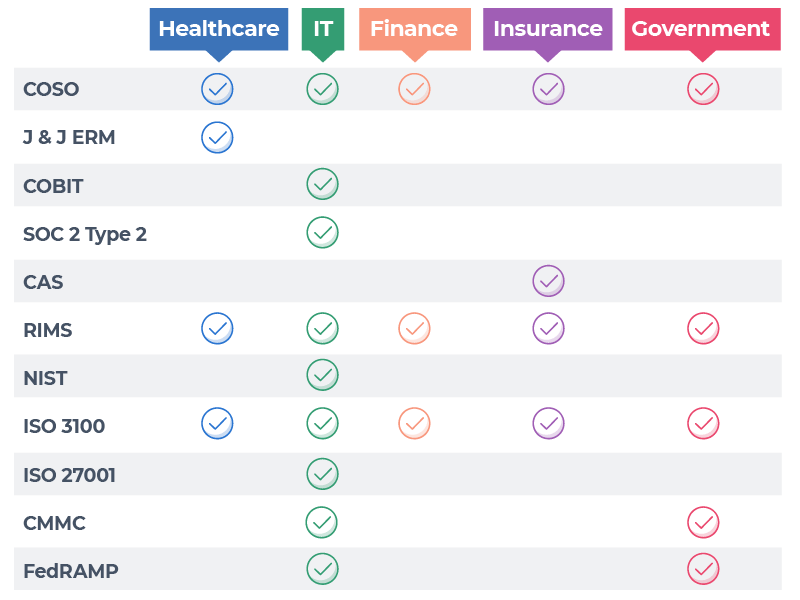
Popular ERM Framework Examples by Industry
Enterprises of all types and sizes face external and internal risks, regardless of industry. However, some ERM frameworks are more prevalent across specific industries due to privacy laws, financial transactions, the regulatory environment, and governance requirements for technology and infrastructure.
Popular ERM Frameworks by Industry
This chart is not an exhaustive dataset. Instead, it highlights the popular ERM frameworks and models discussed in this article and the industries that leverage them to create customized ERM programs.
Enterprise Risk Management Framework for Healthcare
Johnson & Johnson is one of the largest healthcare enterprises in the world. The company created a custom ERM framework, guided by the COSO ERM framework, to address healthcare-specific risks such as reduced business vitality due to healthcare reform.
The Johnson & Johnson ERM framework consists of the following five integrated components:
- Strategy and Objectives: The executive committee establishes strategic goals and financial targets that cascade to global business units through senior management.
- Performance: Establish risk responses with leadership, use risk management functions to implement policies and controls, and develop action plans. The company monitors performance throughout the year using risk assessments, scans, and surveys.
- Review and Revision: Personnel — independent of the business unit they're reviewing — test, audit, and assess risk response performance. They report risk mitigation activities to leadership, and review metrics.
- Information, Communication, and Reporting: Key risk personnel meet the board of directors, executive committee, and business leaders to ensure ownership of ERM programs. They conduct training and exchange knowledge across business units. They use the employee intranet and direct communication to disseminate information.
- Governance and Oversight: The board of directors provides oversight of risk and meets regularly with leadership. The executive committee establishes strategic goals and oversees risk functions of the business sectors. Various committees share emerging risks and standard practices across core risk functions like healthcare compliance.
Enterprise Risk Management Framework for IT
The popularity of IT managed services, software-as-a-service (SaaS) technology, and cloud computing has created a new dynamic for the digital enterprise. Data breaches and IT security compliance should concern every organization, regardless of industry or size.
COBIT by ISACA helps guide information and technology decisions that support and sustain business objectives. COBIT is comprehensive and provides a governance and management framework for enterprise IT that adds value to all information and technology decision making.
The COBIT framework helps maintain the balance between realizing benefits, optimizing risk, and using IT resources. It consists of a process reference model, a series of governance and management practices, and tools to enable an organization's governance.
The SOC 2 Type 2 ERM Model
SOC 2 Type 2 is an IT compliance and security model that ensures that IT and SaaS vendors (or any technology “as-a-service” provider) securely manage data. This set of criteria, composed of five principles, was developed by the American Institute of CPAs (AICPA). These principles include security, availability, processing integrity, confidentiality, and privacy.
Responsive Cybersecurity Frameworks
Sean Cordero has seen industry standards and certification bodies rise to meet the demand for less prescriptive, more flexible risk management. He helps lead the core research team for risk control development with the Cloud Security Alliance (CSA), a leading authority in cloud security.
“When you're doing this kind of research, you do it because you want to make a difference,” he says. “It becomes extremely complex to start making changes at scale when you start talking about overarching standards that go through multiple certification bodies where they have an attestation program and third-party validation.”
According to Cordero, the certification process impedes going to market with an MVP or a software feature request.
The combination of lagging standards without frequent updates, changing security processes, and outdated security technology and tools (for example, vulnerability scanners) creates questions that more responsive ERM frameworks might be able to address.
Flexible IT Frameworks
“We're at an interesting inflection point in the security industry,” says Cordero. “Is this a failure of standards, or a failure of technology, or is it both? Because of the inflexibility of certain risk frameworks, or control frameworks, and the existing technology overlaid on top of both, it is almost impossible to enforce the majority of control standards out there.”
Cordero knows firsthand that there's a movement in risk management and security control frameworks to be less prescriptive and provide more implementation guidance through his research work with Cloud Security Alliance.
“We're no longer saying, ‘You must do these 15 things or you don't meet this requirement,’" he explains. "Instead, we're saying, ‘You must use industry-validated encryption for business and customer sensitive information.’ We're not defining ‘business-sensitive.’ That's for you to decide."
Cordero also points out that control standards still provide value. That said, those that just get grandfathered into existing frameworks are not sustainable in a cloud-first world, as they were intended for a different world and a different approach.
Regarding ERM frameworks and the risk management approach to the industry as a whole, Cordero believes one of the things that's always been a problem is the idea of customizing a framework or a control.
“It is ultimately just a baby step of the risk management process,” he says. “The framework might provide validation or insight in terms of the time, money, and resources spent. I would advise companies to think about the fact that you can drive yourself insane trying to take a control framework and figure out how to implement all of this stuff.”
ERM Framework for Credit Unions, Banks, and Financial Institutions
Risk management is a vital part of running an enterprise-scale credit union. Section 704.21 of the National Credit Union Administration's (NCUA) rules and regulations require credit unions to develop and follow an (ERM) policy.
ERM frameworks like COSO enable a holistic view of enterprise risks for financial institutions and credit unions to measure and analyze the risks impacting various functions. A well designed ERM framework provides the corporate board of directors and senior management with a process to determine the following:
- The amount of risk exposure
- The maximum levels of risk appetite
- How the risk exposures change and the appropriate risk controls to manage change
The Barclays ERM Framework
The COSO ERM framework was adapted by prominent enterprise financial institutions like Barclays, an international bank, and customized to leverage ERM components that drive business value and meet regulatory compliance standards. Barclays uses their ERM framework to manage the following types of risk:
The Barclays Board Risk Committee is a group of non-executive directors that issue an annual report based on the Barclays ERM framework, financial governance codes, and the disclosure guidance and transparency rules of the financial regulatory bodies in which they operate. The committee is responsible for recommending risk appetite to the board, monitoring Barclays' financial, operational, and legal risk profile, and providing input on financial and operational threats and opportunities.
The Deloitte Legal ERM Framework
In 2018, international consulting conglomerate Deloitte created a legal risk management framework. The Deloitte legal ERM framework was developed in response to increased risk management expectations. The framework gives Deloitte a competitive advantage because it controls legal risks across enterprise operations.
The Deloitte legal ERM framework has the following four components:
- Identify: Define legal risk, understand the legal risk universe, and ensure ownership of legal risk between functional business units, such as compliance.
- Assess: Set the legal risk appetite threshold, define it, and embed a legal risk assessment process to determine risk exposure against a set of legal factors.
- Control: Embed a control framework based on the legal risk appetite, and create controls based on technology for legal risk control.
- Monitor and Report: Use a defined methodology to assess the effectiveness of legal risk controls, report legal risk profiles, and control the environment's success to designated stakeholders.
Enterprise Risk Management Framework for Insurance Companies
The insurance industry is still beginning to embrace comprehensive ERM frameworks that do more than meet compliance standards. Most insurers use an internal risk and solvency assessment (ORSA) policy to meet U.S. regulations and governance requirements.
ORSA helps insurers assess risk management capabilities and evaluate market risk, credit and underwriting risk, liquidity risk, and operational risk. However, ORSA is limited to an early stage risk management program for standard compliance compared to comprehensive ERM frameworks like CAS and COSO ERM frameworks.
These frameworks provide systematic risk-return optimization strategies and tools that align with business objectives and provide value for the insurer and their clients. Insurers that embrace ERM frameworks like COSO create comprehensive risk capital models that support risk management as a valuable business strategy.
ERM Model for Insurance Companies
Risk capital models measure the amount of capital an organization needs to meet business objectives, given its risk profile. You can use them to develop risk strategies and compare internal assessments of risk. They can also rate agencies and regulatory requirements for risk capital to determine risk profiles.
Many insurance organizations rely on some form of risk capital models as a form of ERM. Risk modeling helps define risk by gathering and analyzing data that provides insights on the interactions or risk and business objectives. Risk capital models help provide a framework to support an insurance organization's risk profile and risk appetite, and also help establish a risk culture.
Integrated ERM Framework for Government Organizations
U.S. federal agencies and their leaders are responsible for managing enterprise-scale missions that impact various industries. ERM frameworks, like the cybersecurity maturity model certification (CMMC) and FedRamp, help government agencies assess risk and identify threats and opportunities through ERM programs that align with agency goals and objectives.
The CMMC ERM Maturity Model
CMMC is a more recent cybersecurity risk framework developed by the Under Secretary of Defense for Acquisition and Sustainment, the DoD, and other stakeholders to measure the cybersecurity maturity of government agencies and industry organizations doing business with the federal government. The model provides maturity processes, cybersecurity best practices, and inputs from the security community and multiple security industry frameworks and models.
The CMMC framework uses the following five levels of processes and practices to measure cybersecurity maturity:
- CMMC Level One:
- Processes: Performed
- Practices: Basic Cyber Hygiene
- CMMC Level Two:
- Processes: Documented
- Practices: Intermediate Cyber Hygiene
- CMMC Level Three:
- Processes: Managed
- Practices: Good Cyber Hygiene
- CMMC Level Four:
- Processes: Reviewed
- Practices: Proactive
- CMMC Level FIve:
- Processes: Optimizing
- Practices: Advanced Proactive
The FedRAMP Program
The Federal Risk and Authorization Management Program (FedRAMP) provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud computing products and services. FedRAMP emphasizes cloud security and the protection of federal information when agencies and enterprise partners adopt cloud solutions.
The program supports cloud service providers with an authorization process and maintains a repository of FedRAMP authorizations and reusable security packages. The goal is to facilitate collaboration across government agencies with use cases, tactical cloud-based solutions, and a contractor marketplace.
ERM Integrated Framework Application Techniques
Refactr works with the DoD and government agencies that require strict risk management frameworks and governance practices. Michael Fraser identifies how the application of Refactr's ERM framework and security programs map between partnerships with the DoD and private enterprise clients.
“In some ways, the DoD is more stringent, but depending upon the type of customer, like a financial firm, they may have requirements that are on par with some of the DoD's requirements,” Fraser explains. “Different government organizations recognize different ERM frameworks, including NIST and COSO. Custom frameworks can satisfy their risk compliance standards as well.
“Whether it's the Air Force or a cybersecurity vendor, there's a set of requirements that you have to be able to provide, with the information they understand, that verifies that you use some sort of risk framework. A cybersecurity vendor probably works within multiple different frameworks. The key is to have enough information to impart due diligence for a security program, while trying to abide by industry best practices that map to a particular framework.”
Continuous Risk Management Models
According to Fraser, there are points in time during audits that use compliance frameworks (like FedRAMP and SOC 2 Type 2) when everything is based upon integrity.
“That's where automation comes in,” Fraser says. “To help get to a certain threshold of automated coverage for a particular framework. That's a sufficient, ongoing due diligence process, even if there are always going to be some manual steps inside of the compliance framework.”
For Fraser, there's a difference between trying to check all the boxes of a compliance audit and having a certain percentage of continuous automation coverage within your risk management and security framework.
Fraser highlights the importance of flexibility and a customer-first perspective. Ask yourself: Do you go for an arduous standard like FedRAMP because it provides the highest compliance standards for an audit, or is SOC 2 Type 2 sufficient? “Customers say, well, you're FedRAMP compliant, cool,” he says. “I'm willing to engage with you, even though you don't have SOC 2 Type 2, because FedRAMP is more arduous, a higher bar.”
Fraser recommends that companies reuse a percentage of their custom ERM framework for future internal needs and customer criteria. “Knowing what you need in the longer term is critical for you to know what you need to within the next 30, 90, or 180 days,” he says.
Easily Track and Manage ERM Framework Components with Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.