What Is Vendor Risk Assessment?
Vendor risk assessment (VRA), also known as vendor risk review, is the process of identifying and evaluating potential risks or hazards associated with a vendor's operations and products and its potential impact on your organization.
When you perform a third-party vendor risk assessment, you determine the most likely effects of uncertain events, and then identify, measure, and prioritize them. Potential risks include the accuracy and reliability of operational, customer, and financial information; security breaches, operations effectiveness; and legal and regulatory compliance. By performing vendor due diligence and monitoring (particularly of those that impact your operations), you can help mitigate those risks and provide a solid foundation for productive relationships.
"Every company needs to perform a VRA for all its vendors to ensure smooth business operations and assess potential partner's credibility, security, and privacy protocols, data, and disaster recovery plans," says Salma Suzie Fakhri, author of Supplier Selection Criteria: Pre Qualify Manufacturers, Suppliers and Vendors and Improve Your Sourcing Practices and the Owner and Director of FC2Y, Oceana 144, which sources, procures, purchases, and manages supply chain activities for clients in Australia, China, and the Middle East. "Changes in production, material supply, or processes will affect your supply chain and create disruptions in material flow or other risks," she says.
"A vendor risk assessment is essential in selecting partners that are appropriate to your business needs,” notes Badr Berrada, Founder and CEO of BBN Times. “Most companies need to perform a risk assessment to meet organizational objectives, respect regulations, accurately track projects, and improve their reputation.”
Berrada points out that you should be alert to negative impacts to your reputation based on quality concerns. “As technology changed and the world became more connected, vendors competing on price began using cheaper material options. Supply chains are complex, and the use of substituted materials has made it critical to understand the vendor, risks, and the product you’re purchasing.”
"Part of any vendor assessment should include the ability to prevent, respond to, and recover from a calamity," stresses Dan Weedin, a risk consultant and business continuity expert who works with small and medium-sized businesses. "More than ever, in an interconnected world, the ability to keep the doors open impacts so many other businesses and workers. Establishing clarity in continued operations planning is paramount."
To learn more about how to assess current and potential suppliers read our “Definitive Guide to Vendor Risk Management Strategy and Tips.”
Different Types of Vendor Risk Assessment Reviews
You can use vendor risk assessment reviews to identify the probability and severity of potential hazards and their qualitative and quantitative impacts on a business or organization.
“Probability is a statistical dimension describing how probable or likely is this event to happen,” explains Jon M. Quigley, principal of Value Transformation, a product development training and cost improvement organization. “Severity, just like it sounds, is how painful any particular event can be if this potential becomes a real event.”
“Once an event happens, it’s no longer classified as a risk. Sometimes this point gets confused,” says Quigley. “I’ve often had project team members say, ‘We have a risk,’ but what we [actually] have is a burgeoning failure. The impact of the risk is now in the queue to hit our organization or project. The worst condition? A highly probable event that has a high severity of impact.”
Quigley identifies the broad categories of vendor risk assessment reviews and how they are used to define probability and severity dimensions:
- Risk Identification: “To identify what can go wrong, make use of the historical record, organization process metrics, subject matter experts, and brainstorming-type activities,” Quigley explains. “This identification activity should be performed with a cross-functional team to provide multiple perspectives. The result of the risk identification process is a comprehensive list of potential hazards.”
- Risk Evaluation: “Risks vary in severity and impact on organizational objectives. There’s a proverb that illustrates my point: ‘He who grasps too much lets much fall,’” says Quigley. “I use two risk evaluations as filters to prioritize those things that can go wrong.”
- Qualitative Risk Evaluation: This is an ordered ranking of the identified risks, from highest to lowest impact, which is usually enumerated as 1 through n. Risks at the lower end of the scale have a greater impact and probability of occurrence.
- Quantitative Risk Evaluation: By contrast, this is a risk assessment that connects monetary and dependent impacts on the specific endeavor the organization is undertaking. This approach uses tools like decision tree analysis that produce an expected monetary value (EVM) to support an appropriate decision.
Learn how to take control with “Project Risk Management: Best Practices, Tips, and Expert Advice.”
A Vendor Risk Assessment and Management Team-Building Model
To build an effective vendor risk assessment team, start at the top. Senior management buy-in and enforcement, along with a reporting structure that integrates procurement, risk assessment with vendor management, support strategic overall organizational goals.
Here is a flexible reporting, execution, and delivery model that can be used by companies of any size. This non-siloed model marries procurement to risk assessment to safeguard against hazards throughout the enterprise.
You can grow the size and complexity of the risk assessment and management teams relative to the number and type of vendor and compliance requirements. For example, a multinational pharmaceutical enterprise with multiple products and thousands of vendors requires more detailed risk assessment and oversight teams to comply with state and federal rules and regulations than a small clothing retailer or specialty food shop.
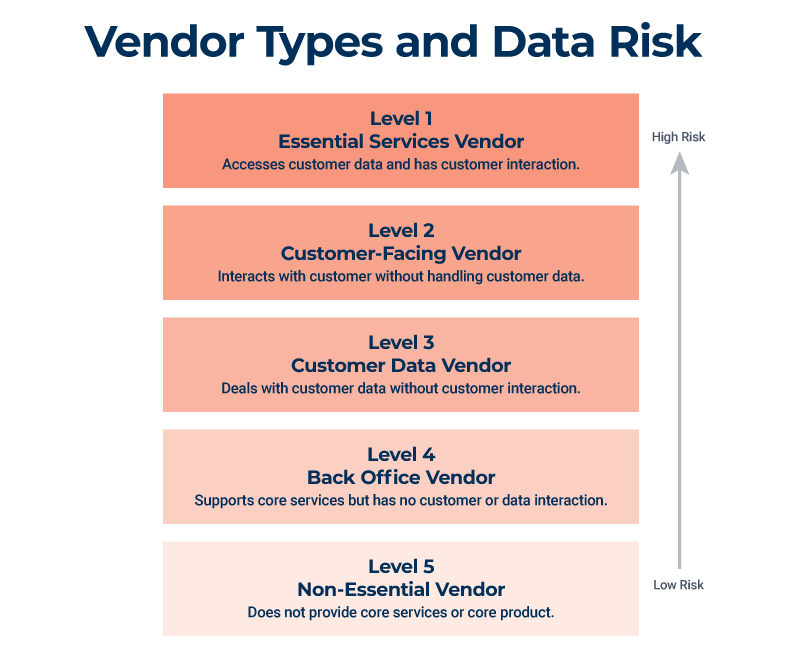
Different Types of Vendors and Risk Impacts
The risk you attribute to different types of vendors depends on different variables, such as the type of business you’re in, the services performed or product provided by the vendor, their importance to your organization, and data security. In other words, there is no absolute risk rating for vendors.
“Risk is subjective — what one organization or industry can tolerate, another can’t,” explains Quigley of Value Transformation. “For example, compare an automotive product development company launching a new anti-lock braking system (ABS) with an online gaming product that does not require personal login credentials. In the former, there are possible system failures [and] potential delivery precision failures to get the product to the manufacturing plant, to name a few hazards that may occur. These can have a serious impact on customers – perhaps even death, in the event of ABS failure.
“The online video game has no material impact, no shipping, no field replacement costs, and so on,” he says.
Assessing Your Vendor Risk Landscape: Vendors can be nearly anyone doing business with your company. These third parties can include the following:
- Manufacturers and Suppliers: They can provide everything from construction materials to cafeteria food.
- Service Providers: Vendors can include janitorial services, paper shredding services, consultants, and advisors.
- Short-Term and Long-Term Contractors: Managing risk means ensuring consistency and visibility, so it’s crucial to hold short- and long-term contractors to the same standards of risk management. Access and other types of secure information may be different for the role a vendor plays, but regardless of the contract length, the rules around access should be the same.
- Vendors of Widely Varying Skills and Backgrounds: This includes IT experts, developers, designers, lawyers, real estate developers, meeting leaders, analysts, sales teams, customer service reps, and more. Essentially, this type of vendor is anyone who provides a service for and to the company while not on staff.
- Contracts of Any Length: The Internal Revenue Service (IRS) has regulations about vendor and third-party relationships that extend beyond specific time frames — this means that, sometimes, the length of a contract can even pose a risk to a company. The IRS’s view is that if a vendor is working onsite, with a company email address, etc., for longer than a specified period of time, then that vendor or independent contractor should be classified as an employee who receives benefits. Each industry has different regulations, so contact the IRS for clarity. However, the IRS often decides that workers are employees if their situations are not clear-cut. This checklist provided by the state of Oregon can help employers decide if a worker is a true independent contractor or third party, or an employee.
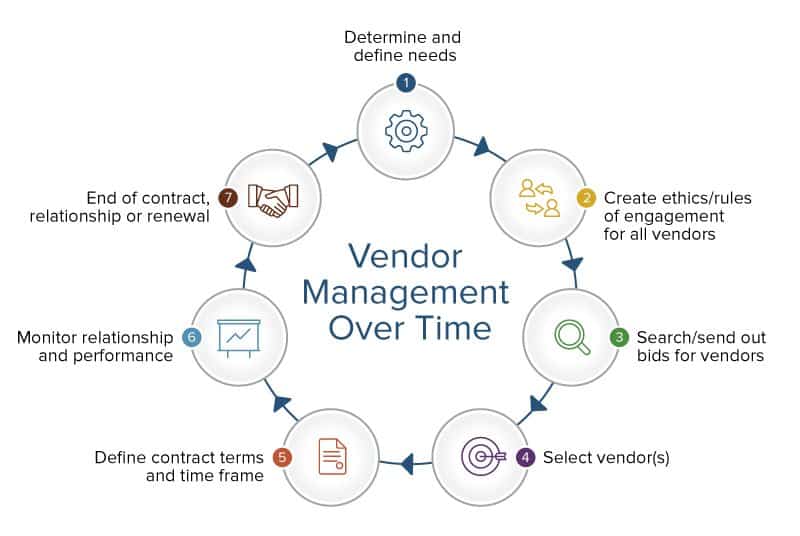
This graphic portrays the lifecycle of a vendor relationship:
BBN Times’ Berrada notes that cyber and data risk are top of mind for his business associates. “Risks are determined based on a threat event, the likelihood of a physical or cyber attack and threats to data and known systems vulnerabilities. Using a strong risk matrix helps organizations identify risks and determine when they require mitigation.”
Protecting data, particularly customer info, is a fundamental consideration in risk planning. By using a scale to rank vendors according to risk, you can focus on which partners need tighter security measures and monitoring.
When to Perform a Vendor Risk Assessment
Perform risk assessments before engaging vendors, on an ongoing, scheduled basis, or when red flags occur in order to uphold standards and contract agreements.
- Pre-Hire Risk Reviews: Introduce risk reviews to vendors during the request-for-proposal (RFP) process. Monitor closely, as a vendor's performance at the RFP is often a strong indicator of future performance. Learn more about the RFP process and how it differs from and works with the request-for-quote (RFQ) process with “Make the Most of the RFQ Process.”
- Red Flags for Risks in the RFP Process: During the initial review, be on the lookout for poor performance tip-offs in RFP responses and the following issues:
- No Process to Protect Data: This indicates that a vendor doesn't value customer security concerns.
- No Internal Risk Assessments: Vendors should have internal risk protocols in place so they are prepared to identify and correct issues as soon as they arise.
- No Formal Security Policy: Data and physical security measures should be standard for every type of vendor.
- No Disaster Recovery Plan: Accident and natural disasters happen — response plans and mitigation measures are necessary.
- Red Flags for Risks in the RFP Process: During the initial review, be on the lookout for poor performance tip-offs in RFP responses and the following issues:
- Ongoing Risk Reviews: "The VRA doesn't stop once the vendor is engaged. Monitor for any variations in agreed-upon deliverables or processes," cautions FC2Y's Fakhri. "Be sure that the vendor is preserving quality standards without generating peril to the company, investors, or customers." Compare your current review to the previous report. If any high-risk items occur, alert business owners and key stakeholders. High-level decision-makers can decide if the relationship continues and determine if it's possible to mitigate risks.
- Regularly Timed Ongoing Reviews: Group and time ongoing vendor reviews according to their designation and renewal date:
- Low-Risk Vendors: Once or twice a year..
- Medium-Risk Vendors: Once or twice a year.
- High-Risk Vendors: Twice a year or quarterly.
- Upcoming Vendor Renewal: 180 days prior to renewal.
- Regularly Timed Ongoing Reviews: Group and time ongoing vendor reviews according to their designation and renewal date:
- Triggered Risk Reviews: Stay vigilant about your vendor’s status. Flag the vendor in Google, and keep abreast of information based on multiple sources, such as word of mouth, business journals, and investment analyst reports. Be on the lookout for the following issues, which should trigger a risk review of current or potential vendors:
- Bad Buzz: Negative press can indicate internal problems.
- Financial Problems: Look out for bankruptcies, layoffs, lowered BBB or Moody’s ratings.
- Flag in Previous Risk Assessment: Make sure the cause of the flag is no longer an issue.
- Legal Issues: Check for lawsuits that name the vendor or critical individuals in the organization.
- Safety Concerns: Look into reports of increased vendor incidents resulting in material or personal harm.
- Short Business History: In business for fewer than three years.
How to Share Vendor RFP and Other Data Files Securely
To assess potential and current vendors and to do business in general, you need to share information with potential partners. Also, make sure that you are handling data securely; email is not a trusted method for data transmission.
The easiest way to maintain security is through the use of data rooms (a form of cloud storage) or an on-premises storage unit to share classified documents. Data rooms can also provide a shared team workspace.
Here are some secure business-grade file sharing methods to consider:
- Box: Users determine how they want to share data. Users can upload files to a shared folder and then either enable view-only access or permit others to view and edit files. Sophisticated security controls, encryption key management, and information governance provide multiple layers of security.
- Citrix ShareFile: Citrix offers a 256-bit advanced encryption standard, a firewall, and antivirus protection. If the site and your files are hacked, the data are useless to the intruder. If a computer is owned or stolen by an ex-employee, you can remotely wipe restricted files from any computer logged in to your account.
- Resilio: This proprietary peer-to-peer (P2P) file synchronization tool works with all operating systems. Resilio syncs files over the internet or between devices on a local network. Within the same network, Resilio has high transfer speeds, and many devices can connect simultaneously. There are no restrictions on the amount of data you can sync, but there is a limit to the amount of data you can store
- Tresorit: Tresors are uploaded directories encrypted in pieces. Tresorit encrypts files using client-side encryption before uploading and automatically syncing them in the cloud when you add or remove data. Users can share protected files and work together on them while keeping the files synced and secure, thanks to end-to-end encryption.
These share rooms offer a free trial, so you can try before you purchase.
How to Perform the Risk Assessment Process
The risk assessment process involves cataloging vendors, understanding their risk in light of your business operations, and creating reports to decide to contract or renew vendors.
Before starting the risk assessment process, set yourself up for success. Ensure buy-in from the entire organization, including top executives, about the vendor risk assessment framework you will use. Decide how to monitor, conduct feedback and reviews, and pinpoint and resolve risks. Apply the same risk criteria to all vendors and adapt measures to the type of product or service when you outsource from different third-party sources.
1. Catalog and Rank Vendors: When companies don’t keep tight control of procurement and relationships with third parties as they grow, the list can become long and unwieldy — and risky. By slimming down your vendor list, you save time, money, and potential headaches.
- List All Current Vendors: Note what each vendor does for your organization, who within your organization owns the relationship, which vendors have access to critical information, and whether or not the vendor manages essential business operations.
- Determine Your Most Critical Vendors: Take a look at your vendor roster. Evaluate whether the unexpected loss of each vendor would cause a material disruption to your company and if the loss would impact customers. Consider how long it might take (i.e., days, weeks, or months) to recover from the loss.
2. Understand Risk Types, Tolerance, and Criteria: “Invest time to look at your business and risks before assessing your vendors,” Weedin advises. “Consider your industry — is expansion or recession in the outlook? — and external factors, such as economic cycles and market conditions, advancement in technology, and supply costs. Review the nature of your operations, ownership structure, organizational governance, and overall financial health.”
Companies of every size face hazards that stem from their use of third-party vendors. Those risks may include the following:
- Operational Risk: These are the uncertainties and hazards your organization confronts doing business everyday within your given field or industry. Operational risks can include potential losses as a result of personnel, procedures, systems, and external events.
- IT Disruption or Failure: You can avoid some hardware risks, such as physical breakdown or destruction of hardware, through design specifications, rigorous testing, and solid backup systems. Software (and the complex relationships found therein), along with the organizational change that comes with new software implementation, can complicate risk measurement and analysis.
- Data and Privacy Risk: Cyberattacks on IT networks can cost millions. Malware designed for nuisance value can carry out different types of activities, from programs that run spam campaigns to ransomware that encrypts files and demands payment for decryption. Malware can cripple firms’ operations, whether the culprit is a thief or a state actor.
- Fraud and Theft Risk: Fraud is an unfortunate reality for businesses of every size. Vendor fraud can take the form of collusion by your employees to channel cash disbursements to a vendor. Different types of fraud include extortion or bribery, billing schemes to create false payments or check tampering.
- Transaction Risk: This refers to the adverse effect that foreign exchange rate fluctuations can have on a completed transaction before settlement.
- Replacement Risk: This is the degree of possibility that one party in a contractual agreement won’t adhere to contract terms and conditions. When this happens, the other party must replace the traded item and potentially incur a loss.
- Upstream Risk: Upstream refers to the material inputs needed for production. Ensure that sufficient inventory is available when you have sudden upticks in your business.
- Downstream Risk: Downstream is where you produce and distribute products. Smaller vendors may not be able to rely on significant backlogs of work or balance sheets in economic or customer downturns. Either work ahead to mitigate downstream risks, or move on to a more solvent vendor.
- Compliance Risk: This refers to legal penalties, as well as financial and material losses an organization faces when it fails to follow industry regulations or laws, internal policies, or prescribed best practices.
- Geographic Risk: Vendors in regions prone to hurricanes, earthquakes, or other natural disasters may pose a risk and require special insurance coverage.
3. Determine Your Risk Tolerance and Rating Criteria: F2CY’s Fakhri uses a three-step process: “First, I determine if the vendor is upstream or downstream; second, I classify them by how critical they are to the business; and third, I develop a risk profile. Risk assessments are usually questions with answers applied to a vendor management risk assessment matrix grid. The answers to those questions yield a point value to help identify the level of vendor risk.” You can find examples of such questions below.
To calculate risk and assign a rating, apply this simple formula to potential risk factors:
Likelihood of (risk factor) x Impact of (risk factor) /Cost = Risk
If your findings are unfavorable, yet the vendor is valuable based on other factors, see if you can work together to mitigate potential hazards.
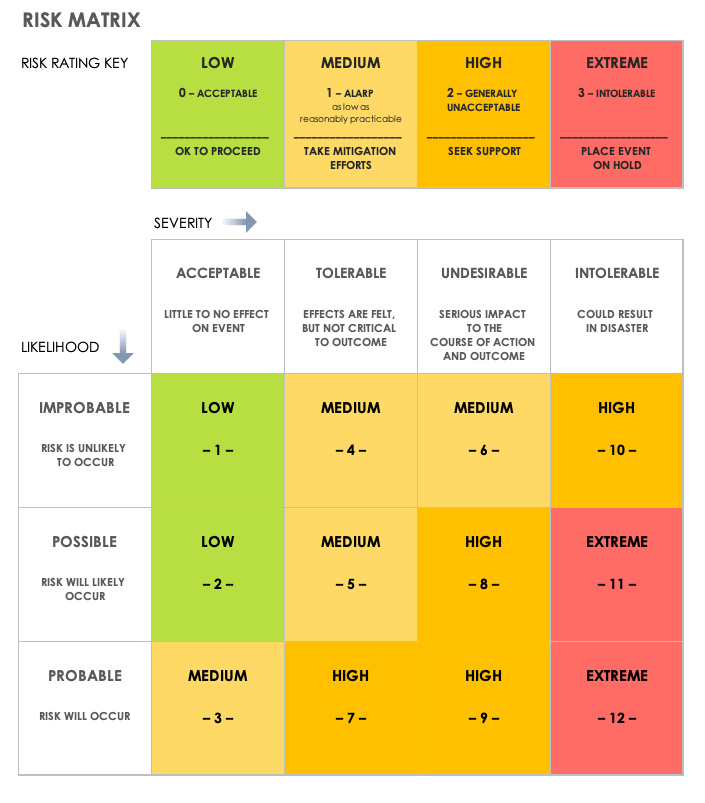
Risk Assessment Matrix Template
This risk assessment matrix template uses a 3x4 non-numeric scale to measure severity and likelihood ranked low, medium, high, and extreme. After you select options for each criterion, use the matrix values to evaluate the level of severity for each risk.
Download 3x4 Risk Assessment Matrix Template - Excel
For more information and risk templates, refer to “Download Free, Customizable Risk Matrix Templates.”
4. Profile Key Vendors: “It’s essential to check feedback, reviews, and press releases from previous clients to determine credibility. Evaluate the effectiveness of incident, environmental, and human resource security to check compliance with business policies and other relevant regulations,” says BBN Times’ Berrada. “Use a flexible inspection app to streamline your risk assessment process. An app will save time on paperwork, risk management, and due diligence protocols.”
You can use the following methods to formally determine whether to keep existing vendors or engage new partners:
- Categorize by Service Type: Designate current and potential vendors based on the product or service they presently or are projected to provide to your company.
- Access Company Data: Research information about potential vendors using direct research, the internet, and other research tools, business relationships, and investment analysts.
- Perform Due Diligence: Address the potential risks you’ve uncovered and discuss them with the vendor.
- Conduct On-Site Audits: When a vendor is a top selection, view their operations in person and meet personnel to help you make a final decision and check off any other items.
5. Compare Top Vendor Contenders: Based on your research, designate a risk profile for each potential vendor. “Companies need to move beyond the pure price model when it comes to supplier selection,” stresses Quigley. “In my experience, any price benefit will evaporate when the first, not even traumatic or risky, event happens. To gain some insight, have a list of attributes you find desirable.”
FC2Y’s Fakhri recommends creating a profile of the perfect vendor based on your current and projected needs to use as a standard, and to prep for future RFPs.
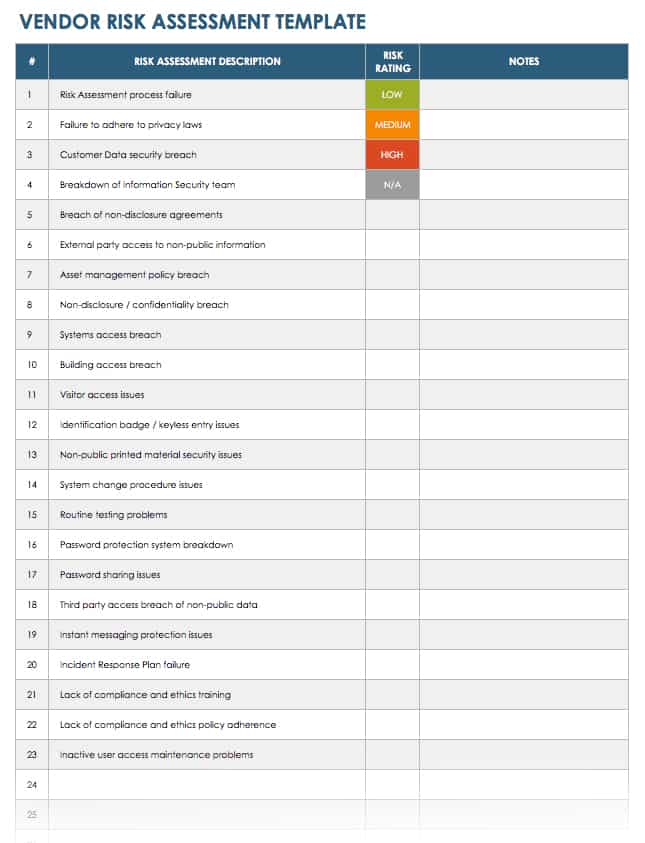
Vendor Assessment Template
Use this template, also known as a third-party risk assessment, to collect assessment descriptions to identify the weaknesses of specific vendors. Assign ratings to each risk description by using the color-coded key, and add notes to share with your team. Use this Excel template to analyze your entire vendor roster, and tailor the description to suit your needs.
Download Vendor Risk Assessment Template - Excel
For more vendor risk assessment templates, view “Free Vendor Risk Assessment Templates.”
Vendor Risk Assessment Reports
Vendor risk assessment reports engage, rank (or rerank), or remove vendors from your roster. A vendor management officer or chief procurement officer should compile and manage the final risk assessments.
With vendor risk assessment reports, you can conduct, write, and present them in four ways:
- By Risk Level: Based on a risk matrix (similar to the one included earlier in this article), you can deliver a brief report that shows risk level based on research and supporting information about how you arrived at your conclusions.
- By Broader Risk Assessment Analytics: This report features ranked criteria, such as quality, turnaround times, customer service, innovation, or other mission-critical assessments. This can provide great value and reveal which vendors support peak operations.
- By Data and Internal Systems Risk: If cybersecurity is a priority for your organization, rank vendors based on RFP responses, your research questionnaire, references, and interviews. You can face risks of compromising customer’s identification, credit card, and health status with stored or transmitted data. Data breaches can create massive headaches, not to mention financial and legal losses.
- Hybrid Report: This is a compilation of all three types of reports and provides a complete picture you can use to judge vendor suitability. A hybrid report can be the best approach for organizations that need to reach a minimal risk level of exposure (e.g., healthcare, finance, or the military).
Risks are present throughout the lifecycle of any purchased product or service, so the more detailed the reports, the better. While consistent and thorough reporting requires time and money, the return on investment in operational excellence and risk reduction is worthwhile.
Vendor Risk Assessment Questions
By asking the right questions regarding crucial areas, like governance and security, you can identify a vendor's level of risk and establish a framework to make decisions that support company goals.
When you are ready to hire a new vendor or third-party provider, it’s time to begin your due diligence. To get security-specific answers, research potential vendors before entering into any contracts to learn how diligent they are about protecting themselves and their partners. Learn more about how to perform a vendor risk assessment with the “Definitive Guide to Vendor Risk Management.”
FC2Y’s Fakhri bases her risk assessment approach on the 5W1H (who, what, when, where, why, and how) question method or Kipling method. The 5W1H method provides multiple points of reference that individuals or teams can use to identify and define qualitative or quantitative risks.
Here are some questions you can draw from to create a customized vendor questionnaire or checklist, with an emphasis on the cybersecurity that is top of mind for many businesses:
References
- Who are your references? Please provide individual names and contact information.
- What is the evidence of financial solvency that can be provided, including recent financial statements?
Performance
- What is your percentage of on-time delivery?
- What contract stipulations, including terms, renewal and notification requirements, and required service levels, can you meet?
- What are your client and internal communication protocols?
- What project management process documentation will be provided for review?
Compliance
- When can we review your liability insurance to ensure that it’s up to date?
- What is your ability for verifying necessary licensing and regulatory compliance, such as governmental security clearance, financial regulatory compliance, or HIPAA training?
- When can we obtain criminal and background checks, including any history from lawsuits, complaints to the state attorney general, or Better Business Bureau records, to demonstrate a history of compliance?
Disaster Preparedness
- What is your readiness strategy for business continuity in the event of a widespread outbreak of disease?
- What are your disaster recovery processes, policies, and procedures for recovery or technology infrastructure continuation after a human-made or natural emergency?
Security Processes
- Do you have incident security breach management practices in place?
- What is your organizational security process? Can we review any relevant documentation?
- Who is in charge, and who receives training in the handling and safeguarding of customer information and procedural breaches?
- What are the physical security procedures that define security for offices and data centers? How do you handle visitors, access to premises, and surveillance?
- What is the asset management process of operating, maintaining, upgrading, and disposing of digital assets or other valuables?
Cyberthreat Governance and Organizational Structure
- Who is responsible for security and cybersecurity within the organization?
- Who is the chief information security officer or chief information officer?
- What can you tell us about any teams or committees that meet regularly on cybersecurity issues?
- What cybersecurity policies do you employ?
- Where do you outsource IT or IT security functions?
- When and how frequently do you train employees on your IT security policies? Do you automate assessments?
- Who on your senior executive team participates in cybersecurity exercises?
- What is your prioritization process to protect your critical assets?
- What standards do you use to protect customer information?
- What has been your most significant cybersecurity incident?
Security Controls and Technology
- Who is in charge and how do you use cybervulnerability and cyberthreat information?
- When and how do you perform inventory on authorized and unauthorized software and devices?
- What practices have you developed to secure configurations for hardware and software?
- What do you use to assess the security of the software that you develop and acquire?
- What processes do you use to monitor the security of your wireless networks?
- What are your data recovery capabilities?
- What automated tools do you use to continuously monitor for malware? What processes and tools do you use to reduce and control administrative privileges?
- What processes do you have in place to prevent sensitive data exfiltration?
- What are your cybersecurity incident plans and preparations?
- What processes do you have in place to respond to an incident? Do you regularly practice those processes?
- When do you conduct external and internal tests to identify vulnerabilities and attack vectors?
- What do you use to manage remote access to your corporate network?
- What are your removable media policies and controls?
- When and how do you monitor for unauthorized connections, devices, personnel, and software?
- What is the process you have in place to communicate security incidents affecting our data?
Download Vendor Risk Assessment Checklist
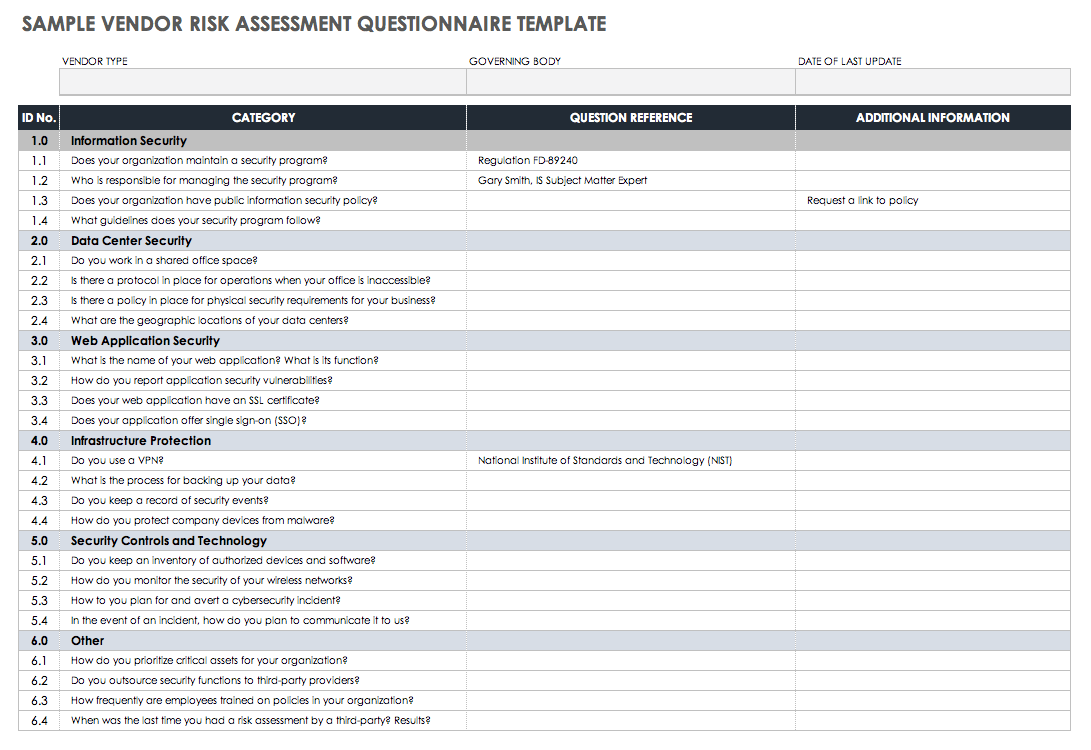
Vendor Risk Assessment Questionnaire Template
You can customize this Excel template to match questions that meet your organization’s risk management structure and align with the RFP you submit to prospective vendors. Easily add more items or a separate category to expand the questionnaire and support your efforts to find the right vendor that provides goods and services and a level of risk that fits your tolerance.
Download Vendor Risk Assessment Questionnaire Checklist - Excel
Vendor Risk Assessment Best Practices
If you're new to the assessment process, by performing due diligence, selection, and ongoing vendor monitoring, you can lower your organization's exposure to business and safety hazards.
Our experts weigh in on best practices to help your organization prepare for any eventuality:
- Plan Risk Response Options Before Risk Occurs: Value Transformation's Quigley recommends that organizations should have a response plan once they understand potential risks. Here are his suggested risk response options:
- Risk Acceptance: When a risk is improbable or the impact is negligible, you can choose to take no action.
- Risk Avoidance: When it is possible to avoid risk, you can employ a different strategy or tactic to eliminate an identified risk. This may open up other, more palatable risks.
- Risk Transfer: Insurance and outsourcing can mitigate or eliminate risk. Even when outsourced, the vendor may still not deliver on the contracted work, and this resulting risk may impact the organization. Risk transfer may provide legal recourse or other avenues of negotiation. While outsourcing does not eliminate the risk, it may reduce the risk when the supplier has more resources or competency.
- Risk Reduction: You can take actions in advance to reduce the severity of the probability of the anticipated risk or risks.
- Risk Contingency Fund: You can secure funds, should risks occur. Calculate the contingency fund by multiplying the probability of the risk coming to fruition, with the anticipated monetary impact. For example, if outsourced work to a supplier that has a $500,000 effect, with a 30 percent probability of failure (such as late delivery), the contingency budget would be $150,000.
- Relationships: FC2Y’s Fakri’s top recommendation is as follows: "Relationship building with vendors." Goodwill is a success factor that has no tangible metric but may make a difference at crucial points in the life of your business.
- Make No Assumptions: Weedin and Fakhri both note that one of the greatest overall risks to any enterprise is to omit vendor assessment reviews from the procurement process altogether. “Many of my clients are now just working on adding vendor risk assessments to their management standards,” Weedin muses. “In their minds, it simply wasn’t a priority.”
Many companies have been unaware or slow to adopt a VRA process, and as Fakri notes, “Companies have mistakenly tended to value cost savings, short time frames, and visual appearance over quality.” - Pondering a Pandemic: In the event of a pandemic or other public health crisis, “It’s important to identify risks and hazards associated with each process and determine if they still fit with company requirements,” BBN Times’ Berrada stresses. “Organizations should question whether customer demands are realistic or reflective of underlying uncertainties of the times. Continuous vendor review is necessary to ensure a safe organizational environment and avoid supply chain issues now or during any other future cataclysm.”
Weedin has seen a difference in his client’s approach since the beginning of 2020. “Make sure your inventory levels are at some range past what you might normally need. Many of my clients were adding 2-4 more weeks to deliveries once the crisis hit. Some wanted but couldn't get goods or services. At this point, we’ve all learned the value of a highly transparent communication plan to keep everyone apprised of operational issues ahead.”
Improve Your Vendor Risk Assessment with Real-Time Work Management in Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Any articles, templates, or information provided by Smartsheet on the website are for reference only. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability with respect to the website or the information, articles, templates, or related graphics contained on the website. Any reliance you place on such information is therefore strictly at your own risk.
These templates are provided as samples only. These templates are in no way meant as legal or compliance advice. Users of these templates must determine what information is necessary and needed to accomplish their objectives.